Public Wi-Fi networks, often found in coffee shops, airports, and hotels, provide convenient internet access but come with inherent security risks. Without encryption, data transmitted over these networks can be intercepted by unauthorized individuals. This interception, known as “eavesdropping,” allows attackers to capture sensitive information such as passwords, credit card numbers, and personal messages.
Most public Wi-Fi networks use a shared password, making them less secure than private networks. Even when a network employs WPA2 encryption, the shared nature of the password compromises its effectiveness. Advanced Persistent Threat (APT) actors and cybercriminals can deploy tools like packet sniffers to monitor network traffic and capture data from unsuspecting users.
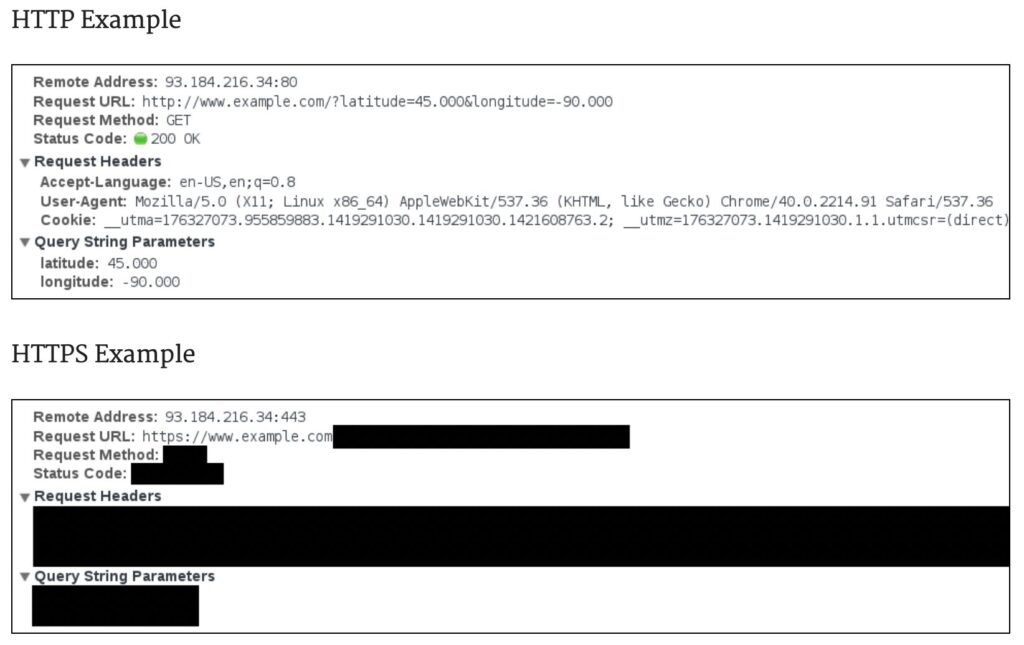
The deployment of HTTPS by many websites has mitigated the risk of data interception to some extent. HTTPS encrypts data between the user’s device and the website, protecting the contents of web traffic. However, not all websites use HTTPS, and attackers can exploit this, particularly through “man-in-the-middle” (MITM) attacks. In a MITM attack, the attacker intercepts communication between two parties, either to spy on the data or to impersonate one of the parties, making sensitive transactions vulnerable.
Risks of Using Public Wi-Fi Networks
Public Wi-Fi networks expose users to several risks, primarily due to their lack of stringent security protocols. One of the main concerns is the potential for data interception. Since public Wi-Fi often lacks encryption, or uses it minimally, data sent through these networks can be easily captured by malicious actors. This vulnerability is particularly concerning for sensitive information like login credentials, financial data, and personal communications.
Another significant risk involves the presence of rogue access points, which are malicious Wi-Fi hotspots set up by attackers to mimic legitimate networks. Unsuspecting users connecting to these networks can have their data intercepted or be subject to phishing attempts and malware distribution. These access points are a favored tool for cybercriminals aiming to harvest personal information.
Man-in-the-middle (MITM) attacks are also more feasible on public Wi-Fi. In this scenario, an attacker intercepts the communication between a user’s device and the network, allowing them to spy on data transmissions, manipulate traffic, or insert malicious content. The inherent trust users place in network connections makes MITM attacks particularly effective and dangerous on public Wi-Fi.
Session hijacking is another threat where attackers exploit cookies to take over a user’s session, gaining unauthorized access to accounts and services. Since cookies often transmit over networks unencrypted, attackers can snatch them from the airwaves and impersonate the user, potentially accessing sensitive accounts without needing a password.
Malware distribution is facilitated on public Wi-Fi networks through vulnerabilities in the network or by tricking users into downloading seemingly legitimate software that contains malicious code. Once installed, malware can wreak havoc, from spying on users to locking out critical files in ransomware attacks.
Public Wi-Fi can be used to launch phishing attacks by directing users to fake login pages or deceptive websites. Users, believing they are accessing legitimate sites, enter their credentials, which are then captured by attackers. This technique is often combined with other vulnerabilities present in public Wi-Fi environments to increase the success rate of data theft.
- Man-in-the-middle attacks: Hackers can intercept your data and steal sensitive information like passwords, credit card numbers, and other personal data.
- Malware attacks: Malware can be installed on your device when you connect to a public Wi-Fi network, putting your personal information at risk.
- Rogue Wi-Fi networks: Cybercriminals can set up fake Wi-Fi networks that mimic legitimate ones, tricking you into connecting to their network and stealing your information.
- Unencrypted networks: Public Wi-Fi networks may not be encrypted, meaning that anyone with the right tools can intercept your data and see what you are doing online.
- Sniffing attacks: Hackers can use software tools to monitor your network traffic and steal your sensitive information.
Precautions to Take When Using Public Wi-Fi
Safely using public Wi-Fi requires a combination of technical measures and cautious behavior to mitigate inherent risks. Employing a Virtual Private Network (VPN) is paramount; it encrypts all traffic from a device, making data unreadable to interceptors and protecting against eavesdropping and man-in-the-middle attacks. Choosing a reputable VPN service ensures strong encryption and a secure connection over public networks.
Ensuring that websites use HTTPS is another critical step. This encrypts the data between the web browser and the server, safeguarding the privacy and integrity of the information exchanged. Users should look for the lock symbol in the browser’s address bar or ensure the URL begins with “https://” before entering any sensitive information.
Keeping software and operating systems up to date is essential for security. Updates often include patches for security vulnerabilities that could be exploited by attackers on public networks. This applies to all software, including the operating system, browsers, and any installed applications.
Activating a firewall on devices provides a layer of defense against unauthorized access. Most operating systems come with a built-in firewall, which monitors incoming and outgoing network traffic and blocks suspicious activity. Ensuring the firewall is enabled helps protect against malware and other network-based threats.
Being selective about what you do online while connected to public Wi-Fi can significantly reduce risk. Avoiding sensitive transactions, such as online banking or shopping, can prevent the exposure of financial details or personal information over an insecure network.
Using two-factor authentication (2FA) for online accounts adds an extra layer of security. Even if login credentials are compromised, 2FA requires a second form of verification, typically a code sent to a mobile device, making unauthorized access more difficult.
Being aware of the network you are connecting to can prevent falling victim to rogue access points. Verify the legitimacy of the Wi-Fi network with staff or through official signage before connecting, and avoid networks with suspicious names or no authentication requirements.
Disabling features like file sharing and AirDrop (for Apple devices) and turning off Wi-Fi when not in use can minimize vulnerabilities. These features can be exploited by attackers to gain unauthorized access to your device or to send malicious files.
- Avoid accessing sensitive information: Refrain from accessing sensitive data like banking details or personal email.
- Use a VPN: A virtual private network (VPN) encrypts your data and provides a secure connection to the internet, making it harder for hackers to intercept your information.
- Use HTTPS: Always look for websites that use HTTPS as they offer more secure communication.
- Turn off file sharing: make sure that file sharing is turned off on your device to prevent others from accessing your files.
- Keep your software up to date: Regularly update your device’s software and applications to ensure that they have the latest security patches.
Examples of Where Public Networks May Be Found
Public Wi-Fi networks can be found in a variety of locations, including:
- Coffee shops and restaurants: Many coffee shops, cafes, and restaurants offer free Wi-Fi to their customers.
- Airports: Most airports have Wi-Fi hotspots available for travelers.
- Libraries: Public libraries often provide free Wi-Fi for visitors.
- Hotels: Many hotels offer Wi-Fi to their guests.
- Public parks and plazas: Some public parks and plazas have free Wi-Fi available.
- Shopping centers and malls: Many shopping centers and malls offer free Wi-Fi to their customers.
- Public transportation: Some buses, trains, and subway systems offer Wi-Fi for passengers.
These are just a few examples of where public Wi-Fi networks can be found.
Private Networks vs Public Networks
Public Wi-Fi and private Wi-Fi differ fundamentally in terms of access control, security measures, and intended use cases, reflecting their distinct roles in digital communication.
Public Wi-Fi is designed for broad accessibility, offered in places like cafes, airports, and public squares to provide internet access to anyone within range. This open nature inherently limits the security of these networks. Typically, public Wi-Fi lacks rigorous encryption, making it vulnerable to cyber threats such as eavesdropping, man-in-the-middle attacks, and unauthorized access. The minimal authentication required to connect further exposes users to potential risks, including interaction with malicious actors or devices.
Private Wi-Fi is established within controlled environments such as homes or businesses. Access is restricted through encrypted passwords and network settings, significantly enhancing security. Private networks often employ robust encryption protocols like WPA2 or WPA3, providing a secure channel for data transmission. The controlled access ensures that only authorized users can connect to the network, reducing the risk of cyber threats.
Private Wi-Fi allows for customized security settings, including the activation of firewalls, the management of device connections, and the implementation of network filters to block unwanted traffic. This level of control is crucial for protecting sensitive information and ensuring the integrity of the network.
Performance is another area where private Wi-Fi generally surpasses public Wi-Fi. Due to the limited number of users and the ability to manage bandwidth allocation, private Wi-Fi networks often offer faster speeds and more reliable connections. This is particularly important for bandwidth-intensive activities such as streaming, gaming, and video conferencing.
The regulatory and compliance considerations for private Wi-Fi networks, especially in business environments, are stringent. Organizations must ensure their networks comply with data protection regulations, such as GDPR or HIPAA, which mandate strict security measures to protect user data. Public Wi-Fi providers also face regulatory requirements, but the focus is often on ensuring lawful use of the service rather than protecting individual data transmissions.
2024 Data Sources