Malware, short for “malicious software,” refers to any software or code that is designed to damage, disrupt, or gain unauthorized access to a computer system or network. Malware can take many forms, including viruses, worms, Trojans, ransomware, spyware, adware, and rootkits.
Malware can be spread through various means, such as email attachments, infected software downloads, malicious websites, or even physical devices like USB drives. Once installed on a computer or network, malware can carry out a variety of harmful actions, such as stealing sensitive data, modifying or deleting files, hijacking system resources, or spreading itself to other machines.
Preventing malware infections requires a combination of security measures, such as using antivirus software, keeping software up-to-date, being cautious when opening email attachments or clicking on links, and regularly backing up important data.
Types of Malware
There are several types of malware, each with its own unique characteristics and methods of spreading and infecting systems. Here are some of the most common types:
- Virus: A virus is a self-replicating program that infects executable files on a system, spreads through the network or removable devices, and can cause damage to the system or steal sensitive data.
- Worm: A worm is a self-replicating program that spreads through network connections and can cause a significant amount of damage by consuming network bandwidth, overloading servers, or spreading additional malware.
- Trojan: A Trojan is a program that appears to be legitimate but actually has malicious intent. It can be used to steal data, spy on users, or install other malware.
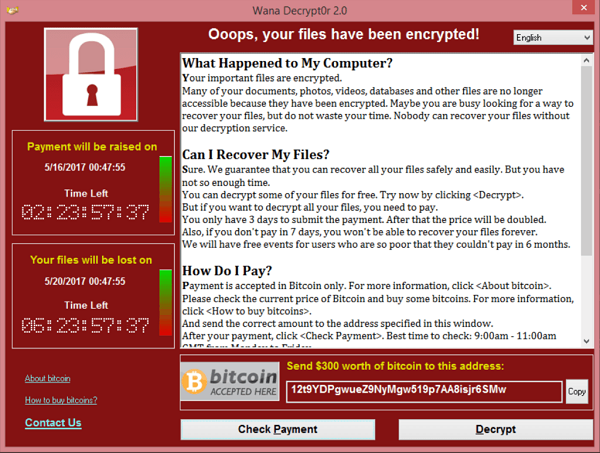
- Ransomware: Ransomware is a type of malware that encrypts a user’s files and demands a ransom in exchange for the decryption key.
- Adware: Adware is a type of malware that displays unwanted ads on a user’s computer, often causing performance issues or exposing the user to additional malware.
- Spyware: Spyware is a type of malware that collects information about a user’s browsing habits, keystrokes, and other sensitive data, and sends it back to the attacker.
- Rootkit: A rootkit is a type of malware that hides its presence from the user and other programs, allowing attackers to gain unauthorized access to a system or network.
Devices and Operating Systems Susceptible to Malware
Malware can infiltrate and affect a wide range of devices including the following.
Desktop and Laptop Computers
Traditional computers, including both desktops and laptops, running on various operating systems like Windows, macOS, and Linux, are primary targets. Their widespread use and the valuable data they often store make them attractive to attackers.
Smartphones and Tablets
Smartphones and tablets, running on platforms like Android and iOS, are increasingly susceptible due to their ubiquitous presence and the wealth of personal information they contain.
Android devices are 50x more likely to be infected with malware than Apple devices running iOS.
Network Devices
Network devices, such as routers and switches, are not immune. Malware targeting these can manipulate network traffic, intercept sensitive information, or create botnets for distributed attacks. Internet of Things (IoT) devices, including smart home gadgets like thermostats, cameras, and lighting systems, often lack robust security measures, making them vulnerable to attacks that can compromise personal privacy or transform them into parts of larger botnets.
Servers
Servers, both on-premises and in cloud environments, are lucrative targets for malware. They can host sensitive data, provide computational resources for crypto-mining malware, or serve as a platform for launching further attacks. Point of Sale (POS) systems and ATMs, handling financial transactions, are targeted for obvious monetary gains. Malware in these systems can lead to direct financial theft or the compromise of payment card information.
Industrial Control Systems
Industrial control systems and critical infrastructure, such as power plants and water treatment facilities, are not typically the focus of widespread malware campaigns but are targeted in sophisticated, state-sponsored attacks. Compromising these can lead to significant disruptions and pose national security risks.
Removable Media
Removable media, like USB drives, can harbor malware that activates when the media is connected to a device. This method is often used to bypass network security measures and directly infect a system. Office equipment, including printers and scanners, might seem innocuous but can be exploited to gain access to a network or to persist within an environment, often unnoticed.
Malware’s adaptability means that virtually any device with computing capabilities and network connectivity can be at risk. This ever-expanding threat landscape necessitates a proactive and comprehensive approach to cybersecurity across all types of devices.
Malware Protection Solutions and Strategies
Protecting devices from malware involves a multi-layered approach that combines software solutions, best practices in digital behavior, and regular system maintenance.
Antivirus Software
Installing and regularly updating reputable antivirus or anti-malware software forms the first line of defense. These tools provide real-time protection against known threats and can detect unusual behavior indicative of new, unknown malware.
There are over 1 billion known malware programs now in existence.
Firewalls
Implementing a robust firewall, either at the network level or on individual devices, is essential. Firewalls act as gatekeepers, controlling incoming and outgoing network traffic based on predetermined security rules. This is particularly important for blocking unauthorized access attempts and limiting the spread of malware within a network.
Software Updates
Regular software updates are crucial. This includes updating the operating system, applications, and any installed plugins. Many malware attacks exploit known vulnerabilities in software, and updates often include patches for these security holes.
Safe Browsing and Cyber Education
Practicing safe browsing habits is vital. This involves avoiding clicking on suspicious links, not downloading attachments from unknown or untrusted sources, and being cautious when providing personal information online. Educating users about the risks of phishing and social engineering attacks can significantly reduce the likelihood of malware infections.
Strong Password Usage and Policies
Strong password policies and the use of multi-factor authentication add an additional layer of security. They make unauthorized access to devices and accounts more challenging, thereby limiting the potential for malware installation through compromised credentials.
80% of confirmed data breaches are due to compromised or weak passwords.
Automated and Frequent Data Backups
Regular backups of critical data are indispensable. In the event of a malware infection, having up-to-date backups can prevent data loss and facilitate the recovery process. It’s important to ensure that these backups are stored securely and, if possible, disconnected from the network to avoid contamination by malware.
Authorized App Installs
For mobile devices, installing apps only from official app stores and avoiding jailbreaking or rooting devices can significantly reduce the risk of malware infections. These practices ensure that apps undergo some level of security vetting, and system integrity is maintained.
Network Monitoring
Network monitoring and intrusion detection systems can provide early warning of suspicious activities that might indicate a malware infection. These systems can monitor network traffic for signs of malware communication or attempts to spread within a network.
Cyberdefense Centric Culture
Maintaining an overall culture of security awareness within organizations and among individual users is fundamental. This involves staying informed about the latest malware threats and understanding the ever-evolving landscape of cyber security. Regular training sessions, updates, and reminders about best practices in digital security can significantly bolster defenses against malware.
Malware Scans
A malware scan is a process executed by security software designed to detect and identify malicious software, or malware, on a computer system or network. During this scan, the security software scrutinizes files, applications, and system memory for patterns or signatures that match known malware. This process can be likened to a detective methodically searching a building, looking for specific signs of unauthorized entry or activity.
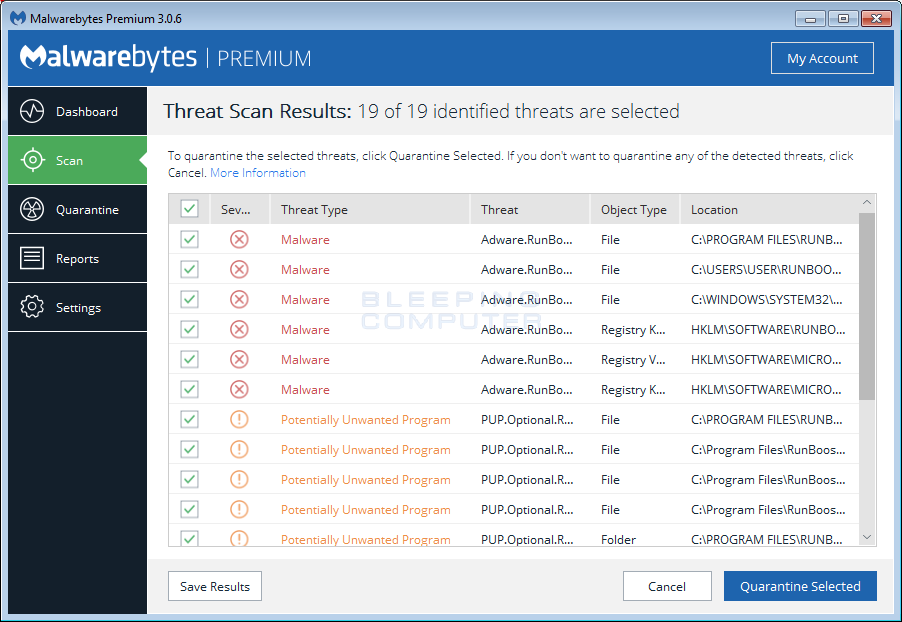
The core component of a malware scan is its database of malware signatures, which are unique strings of data or characteristics that are known to be part of malware. When the security software examines a file, it compares it to the signatures in its database. If there’s a match, it flags the file as potentially malicious. This method is highly effective for detecting known malware but may not always catch new, previously unidentified threats.
To address the limitations of signature-based detection, many modern malware scanners incorporate heuristic analysis. This method involves looking for file behaviors or attributes that are typically associated with malicious activity, rather than relying solely on known signatures. For example, a file that attempts to modify system files or hide its presence might be flagged as suspicious, even if it doesn’t match any known malware signature.
Some advanced malware scanners also employ behavioral analysis, which monitors how programs behave in real-time. This approach can detect malware that tries to evade traditional scanning methods, such as polymorphic malware that changes its code to avoid detection.
Malware scanners often include various scan options, such as quick scans that focus on areas where malware is most likely to be found, like system files and running processes, and full scans that comprehensively check every file and folder on the system. Scheduled scans can be set up to run automatically, ensuring regular system checks without user intervention.
In addition to detecting malware, these scans often assess the overall security posture of the system. They may identify vulnerabilities, such as outdated software or weak passwords, which could be exploited by malware.
Once a threat is identified, the malware scanner typically takes steps to neutralize it. This could involve quarantining suspicious files, preventing them from running, or completely removing them from the system. In some cases, the scanner may also provide recommendations for further action, such as changing security settings or updating software to prevent future infections.
560,000 new pieces of malware are detected daily.
Malware Removal
Removing malware from a device requires a combination of technical know-how and systematic procedures, tailored to the type of device and the nature of the malware.
Desktops and Laptops
For computers running Windows, macOS, or Linux, the first step often involves disconnecting the device from the internet to prevent the spread of the infection or communication with a command and control server. Next, entering Safe Mode is crucial as it loads the system with minimal services and processes, reducing the chance of the malware being active. In Safe Mode, running a reputable antivirus or anti-malware software is the primary method for detection and removal. These tools are designed to identify and eliminate known malware strains.
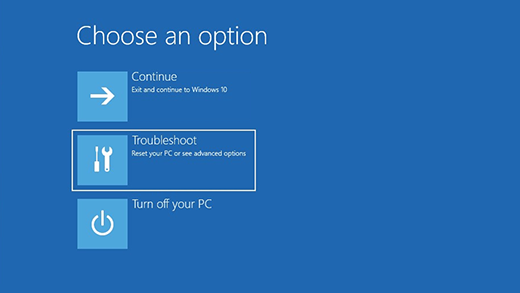
For persistent infections, manual steps might be necessary, including the examination of system logs, startup items, and scheduled tasks. Registry (in Windows) or system configuration files (in Linux and macOS) may need inspection and cleaning. System restore points or backups can be employed to return the system to a state before the infection, but caution is needed to ensure backups are not themselves infected.
Smartphones and Tablets
Smartphones and tablets infected with malware demand a different approach. The device should be restarted in safe mode if available, which prevents third-party apps from running. Then, the suspicious app(s), usually the source of the infection, must be identified and uninstalled. Factory reset is often recommended for severe cases, but this erases all data on the device, so it should be a last resort.
Network Devices
Network devices like routers require a firmware update or a factory reset to remove malware. Updating firmware can eliminate known vulnerabilities that the malware might have exploited. For IoT devices, updating the device’s software, changing default passwords, and performing a factory reset are effective measures.
Servers
Servers infected with malware, especially in enterprise environments, require a more cautious approach due to their critical role and the data they hold. Forensic analysis to understand the malware’s impact and spread is often necessary. Isolation of the infected server, followed by a thorough malware removal process and data recovery from clean backups, is standard practice.
Successful Malware Removal and Future-Proofing
Regardless of the device, after removing malware, it’s essential to change all passwords and review security settings to prevent future infections. Continuous monitoring for unusual activity is advised as malware can sometimes remain dormant or undetected by conventional security tools. Finally, updating all software and maintaining a robust security posture is key to reducing the risk of future malware infections.
2025 Data Sources
- https://www.cisa.gov/topics/cyber-threats-and-advisories/malware-phishing-and-ransomware
- https://consumer.ftc.gov/articles/how-recognize-remove-avoid-malware
- https://csrc.nist.gov/glossary/term/malware
- https://www.ncbi.nlm.nih.gov/pmc/
articles/PMC5041502/ - https://dodcio.defense.gov/Portals/0/
Documents/Library/
CSResourceReferenceGuide.pdf