Communication spam, often referred to simply as “spam,” generally refers to the practice of sending unsolicited, irrelevant, or inappropriate messages to a large number of recipients, typically for advertising or malicious purposes. It’s called “spam” because it fills up your inbox (or other communication medium) with unwanted content, much like the canned meat Spam is often used to bulk up a meal.
Types of Spam
Spam manifests in various forms, each designed to bypass filters, grab attention, or deceive recipients.
- Email spam
- Text message spam
- Social Media spam
- Call spam
- Comment spam
- Search engine spam
- Ad spam
- Image and video spam
Email Spam
Email spam, perhaps the most familiar, involves unsolicited messages sent in bulk, often for advertising, phishing, or spreading malware. Phishing emails, a subset, specifically aim to trick recipients into divulging sensitive information like passwords or credit card details by masquerading as trustworthy entities.
67% of email users say spam has made being online unpleasant or annoying.
Text Message Spam
SMS spam follows a similar pattern, targeting mobile phone users with unwanted texts that can range from promotional content to phishing attempts. Social media spam proliferates across platforms, including unsolicited friend requests, messages, and posts, often automated by bots to spread malware, fraudulent schemes, or to artificially inflate engagement metrics for certain posts or pages.
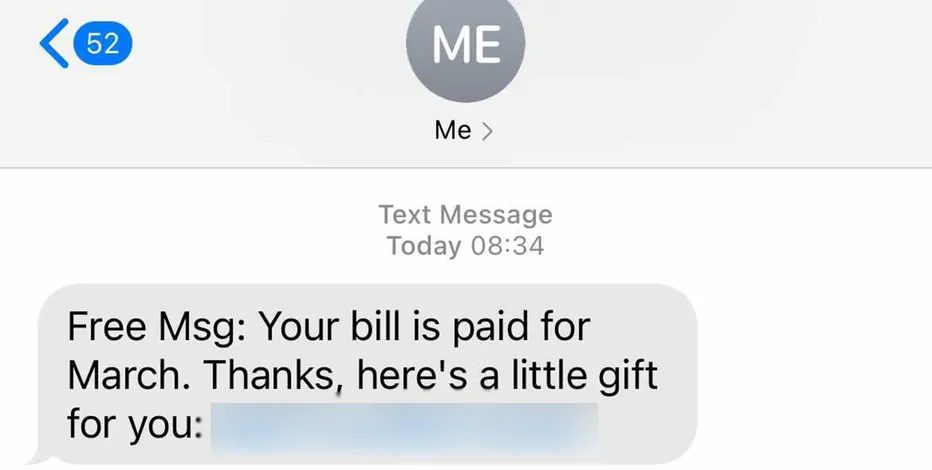
Phone Call Spam
Call spam, often referred to as robocalls, involves unsolicited, automated phone calls made to a large number of recipients, typically for telemarketing, political campaigns, or scams. These calls use pre-recorded messages and, increasingly, voice simulation technology to interact with the recipient.
Comment Spam
Comment spam infests the comment sections of websites, blogs, and forums, where automated bots or individuals post irrelevant links or content, usually to boost the search engine rankings of particular sites or for direct advertising.
Spambots
Spambots and malicious software play a critical role in automating and disseminating spam. These automated programs can create fake accounts, send messages, and post comments at a scale unachievable by humans, often leveraging compromised computers (botnets) to distribute spam widely and evade detection.
Search Engine Spam
Search engine spam, or SEO spam, employs techniques like keyword stuffing, cloaking, and the use of doorway pages to manipulate search engine rankings. This not only degrades the quality of search results for users but also poses a significant challenge for search engines striving to deliver relevant content.
Ad Spam
Ad spam, which includes unwanted pop-ups, banner ads, and redirects, significantly detracts from user experience on websites, often leveraging aggressive or deceptive tactics to generate clicks.
Image and Video Spam
Image and video spam use visual content to bypass text-based filters, embedding messages within images or videos to advertise, scam, or spread malicious links. These spams exploit the more complex analysis required to detect and filter out unwanted visual content, posing additional challenges for anti-spam technologies.
What are the Signs of Spam?
Whether you’re dealing with email, text messages, social media messages, or even phone calls, there are common signs that can indicate you’re dealing with spam. Here are some red flags to look out for:
- Unsolicited communication: If you didn’t sign up for it and don’t recognize the sender, it could be spam.
- Generic greetings: Many spam messages start with a vague “Dear Customer” or “Dear Sir/Madam.”
- Poor spelling and grammar: If the message is riddled with spelling errors, odd phrasing, and bad grammar, it’s likely spam.
- Unrealistic offers: If it seems too good to be true, it probably is. Be especially wary of messages claiming you’ve won a lottery or sweepstakes that you don’t remember entering.
- Requests for personal information: Legitimate companies usually don’t ask for sensitive information like your password, credit card number, or social security number via email or text message.
- Pressure tactics: Many spam messages create a sense of urgency, insisting you must act now or something bad will happen.
- Suspicious links or attachments: These could lead to malicious software or phishing sites designed to steal your personal information.
- Misspelled domain names or email addresses: Spammers often use email addresses and URLs that look similar to legitimate ones, but with minor typos or extra characters.
- No option to unsubscribe: Legitimate marketing emails are required to offer a way to opt out of future communications. If there’s no way to unsubscribe, it’s likely spam.
- Inconsistent formatting: Often, spam messages will have strange layouts, font sizes, or mismatched logos, which can be a sign that the message is not from a professional organization.
If you come across a message that raises these or other suspicions, it’s best not to engage, not to click on any links or download any attachments, and to delete the message. If you’re unsure whether a message is spam, you can always reach out to the supposed sender (via a known, trusted method, not by replying to the suspicious message) to verify.
Spam Protection Strategies and Solutions
There are several strategies to protect yourself from spam:
- Use spam filters: Most email services provide a spam or junk filter that automatically identifies and separates spam emails from your regular inbox. Always make sure this feature is turned on.
- Be careful when sharing your email address: Try not to publicize your email address widely and be cautious about who you give it to. Consider using a secondary email address for signing up for newsletters or online services.
- Don’t open or respond to spam: If you recognize an email as spam before you open it, don’t open it. If you do open a spam email, do not reply or click on any links or attachments.
- Beware of phishing attempts: Be very careful with emails asking for personal information. Legitimate businesses generally do not ask for sensitive personal information over email.
- Update your software: Regularly update your device’s operating system and your email software. These updates often include security improvements that can help protect against spam and phishing attacks.
- Use antivirus software: Install and update antivirus software on your devices. This software can protect against malware that might come in through spam emails or other spam messages.
- Don’t purchase from spammers: Spammers keep spamming because it works. Never buy a product or service from a spam email.
- Report spam: Report spam to your email provider. Most email services have a button to report spam. This not only helps you by improving the spam filter, but it also helps others by improving the overall system.
- Use strong, unique passwords: This helps protect your email account from being hacked and used to send out spam.
- Unsubscribe when you can: If the spam email comes from a legitimate business, there will often be an “unsubscribe” link at the bottom of the email. Use this to stop receiving these types of emails.
These strategies will help you reduce the amount of spam you receive and protect your devices and your personal information.
Spam and the Risk of Identity Theft
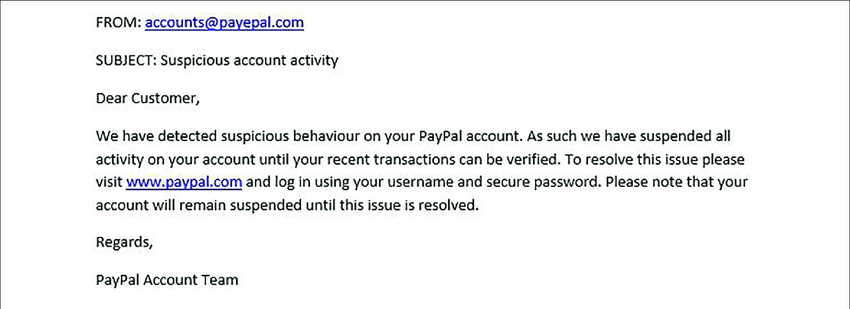
Spam can potentially lead to identity theft through a process known as phishing.
Phishing is a technique used by cybercriminals where they send emails or messages that appear to be from legitimate companies. These messages usually ask you to confirm your personal information, including your password, credit card number, social security number, or other sensitive details. If you respond with the requested information, the criminals can use it to access your accounts, steal your identity, and commit fraud.
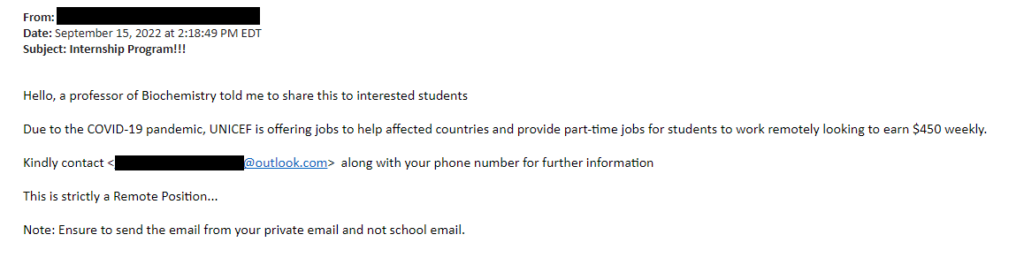
A related technique is spear phishing, where the cybercriminals use information they’ve gathered about you to personalize their messages and make them seem more convincing.
Some spam emails or messages contain links to websites or attachments that, when clicked or opened, can install malicious software (malware) on your device. This malware can capture your keystrokes, access your files, or otherwise gather your personal information, which can then be used for identity theft.
It’s important to be vigilant when dealing with unexpected or suspicious messages, even if they appear to be from a company or individual you recognize. Always double-check the sender’s email address, be cautious about providing personal information online, and avoid clicking on links or opening attachments in suspicious emails. Regularly updating your devices and using security software can also help protect you from malware and phishing attempts.
52% of internet users consider spam a big problem.
What is the CAN-SPAM Act?
The CAN-SPAM Act, short for the Controlling the Assault of Non-Solicited Pornography And Marketing Act, is a law enacted in the United States in 2003 to set national standards for the sending of commercial email. It is designed to combat the proliferation of spam email by establishing requirements for commercial messages, granting recipients the right to have emails stopped from being sent to them, and laying out tough penalties for violations.
Key provisions of the CAN-SPAM Act include the necessity for senders of commercial emails to clearly identify the message as an advertisement or solicitation, provide a valid physical postal address of the sender, and include a clear and conspicuous way for recipients to opt-out of future email communications. The act mandates that opt-out requests be honored within 10 business days, and it prohibits the use of deceptive subject lines and the falsification of header information in commercial emails.
Importantly, the CAN-SPAM Act applies not only to bulk email but to all commercial messages, which the law defines as “any electronic mail message the primary purpose of which is the commercial advertisement or promotion of a commercial product or service.” This broad definition means that the law covers a wide array of email content beyond traditional spam, such as promotional emails from businesses to their customers.
Enforcement of the CAN-SPAM Act is primarily the responsibility of the Federal Trade Commission (FTC), but the act also grants enforcement powers to other federal agencies and state attorneys general. Violations of the CAN-SPAM Act can result in significant penalties, including fines of up to $43,280 for each email in violation of the law.
28% of users with a personal email account say they are getting more spam than a year ago.
Critics of the CAN-SPAM Act argue that it has been less effective than hoped in reducing the volume of spam, in part because spammers operating outside the United States can easily evade enforcement. Nonetheless, the act represents a significant effort by the U.S. government to provide a legal framework to address the problem of unwanted email communications and to protect consumers from deceptive and intrusive email practices.
Reporting Spam
Reporting spam is a critical step in helping email providers, regulatory bodies, and anti-spam organizations combat the proliferation of unsolicited messages. For email spam, most email clients and services include a “Report Spam” or “Junk” button that not only moves the message to the spam folder but also sends information about the email to the service provider for analysis. This action helps improve spam filters and prevent similar messages from reaching other users’ inboxes.
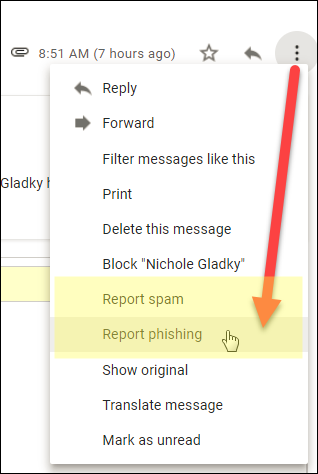
When encountering phishing attempts or more malicious forms of spam, it’s advisable to go a step further by reporting these emails directly to the organizations being impersonated, such as banks, online services, or government agencies. Many of these organizations have dedicated email addresses for receiving such reports, often listed on their official websites.
For more formal reporting, in the United States, the Federal Trade Commission (FTC) encourages individuals to forward spam emails to spam@uce.gov. The FTC uses these reports to build cases against spammers. The Anti-Phishing Working Group (APWG) accepts reports of email fraud and phishing attempts at reportphishing@apwg.org, which helps in the efforts to combat phishing.
For SMS spam, mobile phone users can often forward unwanted texts to 7726 (which spells out “SPAM” on the keypad), a service used by many mobile operators to gather data and block future spam messages from the reported numbers.
On social media platforms, reporting spam can typically be done through the platform’s interface, where users can flag posts, messages, or accounts as spam. These reports are then reviewed by the platform’s moderation team, which takes appropriate action based on the platform’s policies.
In cases of call spam or robocalls, reporting to the national Do Not Call Registry (if available in your country) can be an effective measure. In the United States, complaints can be filed with the Federal Communications Commission (FCC) or the Federal Trade Commission (FTC) via their online complaint forms.
Reporting spam, regardless of the form it takes, not only aids in your own protection but also contributes to broader efforts to reduce spam and protect other users. It’s a key component of digital hygiene and security practices in the ongoing battle against spam and cyber threats.
2025 Data Sources
- https://www.justice.gov/action-center/report-spam
- https://www.fcc.gov/consumers/guides/stop-unwanted-robocalls-and-texts
- https://www.fcc.gov/general/can-spam
- https://www.cisa.gov/news-events/news/reducing-spam
- https://www.donotcall.gov/verify.html
- https://consumer.ftc.gov/articles/how-recognize-and-report-spam-text-messages