A man-in-the-middle (MitM) attack is a type of cyberattack where an attacker intercepts and alters communications between two parties. This can be done by the attacker compromising the connection between the two parties, or by tricking them into connecting to a fake network or website controlled by the attacker. Once the attacker has intercepted the communication, they can read, modify, or inject new data into the communication without either party being aware. MitM attacks can be used to steal sensitive information, such as login credentials or financial data, or to spread malware to compromised devices.
Example of a Man-in-the-Middle Attack
- A hacker creates a fake wireless access point with a similar name as a legitimate one (e.g. “Free Public Wi-Fi” instead of “Free Public WiFi”) and leaves it in a crowded public place.
- A person connects to the fake access point and starts browsing the internet.
- The hacker intercepts all the traffic and can now see everything the person is doing online. This includes login credentials, credit card information, and other sensitive information.
- The hacker can also alter the information being sent, such as redirecting the person to a phishing website or injecting malware into the person’s device.
- In this example, the person thinks he is communicating with the legitimate access point, but in reality, all the communication is passing through the hacker’s device which allows him to see and manipulate the communication.
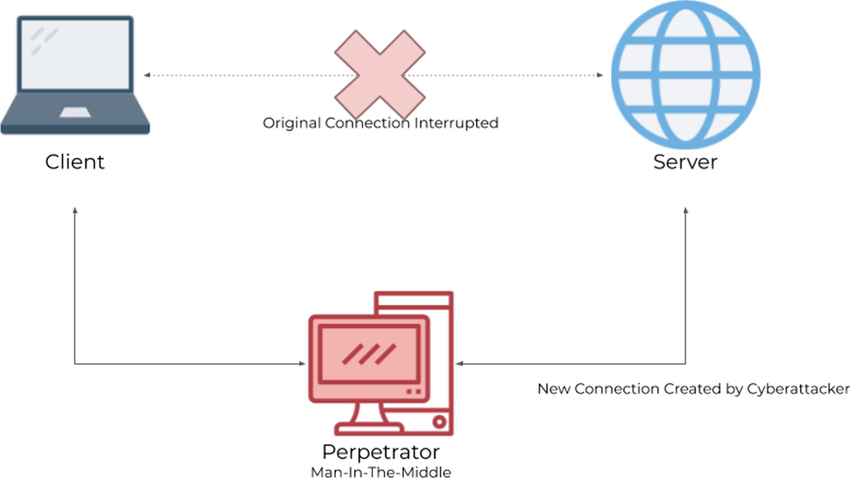
This is just one example of a MitM attack, but it can also be executed in other ways, such as through phishing emails, malicious software, or compromised websites.
Where Do Man-in-the-Middle Attacks Occur At?
Man-in-the-middle (MitM) attacks can occur in a variety of places and contexts. Some common places where MitM attacks occur include:
- Public Wi-Fi networks: Public Wi-Fi networks, such as those found in airports, hotels, and coffee shops, are often unsecured and can easily be compromised by attackers.
- Online networks: In online networks, attackers can intercept and alter communications between two parties, such as between a user and a website or between two users.
- Mobile networks: MitM attacks can also occur on mobile networks, such as when an attacker intercepts communications between a user’s device and a cellular tower.
- In corporate networks: MitM attacks can occur within a corporate network, where an attacker can exploit vulnerabilities to intercept and alter communications between different parts of the organization.
- Phishing scams: Phishing scams are a common form of MitM attack that are used to trick users into giving away their personal information or login credentials.
It’s worth noting that MitM attacks can happen anywhere, regardless of the type of network or device being used, and the attackers can be anyone from individual cybercriminals to nation-states. So it’s important to be vigilant and follow the best practices to protect yourself.
Detecting Man in the Middle Attacks
Detecting a Man-in-the-Middle (MitM) attack involves monitoring and analyzing network traffic, looking for inconsistencies and anomalies that suggest interception or alteration of communications. Encryption irregularities often indicate a MitM attack. For example, unexpected changes in the encryption certificates of websites, especially those using HTTPS, can be a red flag. An attacker may use a forged certificate, so checking the certificate’s validity against known certificate authorities is crucial.
Another method involves examining the latency of network connections. MitM attacks often introduce delays in communication as the data is intercepted and potentially modified. By analyzing network timings and comparing them to known baselines, unusual delays can be identified, pointing to potential MitM activity.
Monitoring IP address inconsistencies is also effective. In a MitM attack, the source or destination IP address might be different from what is expected. Network tools can be configured to alert administrators when packets are not coming from or going to the IP addresses that are expected for a particular service.
Analyzing network traffic for unexpected volume or patterns is another technique. MitM attacks might generate additional traffic or alter the pattern of normal traffic. Employing network monitoring tools to flag significant deviations from normal traffic patterns helps in detecting potential MitM attacks.
MitM attacks account for 19% of all successful cyberattacks.
Incorporating Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) can automate the detection of MitM attacks. These systems use a combination of signature-based and anomaly-based detection techniques to identify suspicious activities that could indicate a MitM attack.
Monitoring for ARP (Address Resolution Protocol) spoofing on local networks is essential. ARP spoofing is a common technique used in MitM attacks to intercept and modify data between two parties on a local network. Tools that can monitor and alert on unusual ARP traffic can be instrumental in detecting these types of attacks.
Protection from Man-in-the-Middle Attacks
There are several ways to protect yourself from a man-in-the-middle (MitM) attack:
- Use a virtual private network (VPN) when connecting to the internet: A VPN encrypts your internet connection, making it more difficult for attackers to intercept your communications.
- Use HTTPS instead of HTTP: Websites that use the HTTPS protocol encrypt the communication between your device and the website, making it more difficult for attackers to intercept your data.
- Be wary of public Wi-Fi: Avoid using public Wi-Fi networks, as they are often unsecured and can easily be compromised by attackers. If you must use public Wi-Fi, use a VPN to encrypt your connection.
- Keep your software and operating system up to date: Regularly updating your software and operating system can help protect you against known vulnerabilities that attackers may exploit.
- Be cautious when clicking on links or downloading attachments: Be wary of clicking on links or downloading attachments from unknown or suspicious sources, as they may be malicious and used to launch a MitM attack.
- Use strong, unique passwords: Use strong, unique passwords for all of your online accounts, and avoid using the same password for multiple accounts.
- Use multi-factor authentication: Multi-factor authentication adds an extra layer of security to your online accounts by requiring a second form of authentication, such as a fingerprint or code sent to your phone, in addition to your password.
2025 Data Sources