Ransomware is a type of malicious software that encrypts the files on a victim’s computer, making them inaccessible and demands payment in exchange for the decryption key. Once the ransom is paid, the attacker will provide the victim with the decryption key to restore access to the encrypted files. Ransomware attacks can cause significant financial and operational damage to individuals and organizations. It’s important to have a backup of your important files and to keep your computer software updated to protect yourself from ransomware attacks.
List of Well-Known Ransomware Attacks
Some examples of well-known ransomware include:
- WannaCry: This ransomware attack affected more than 200,000 computers in 150 countries in 2017. It exploited a vulnerability in older versions of the Windows operating system and spread rapidly through networks.
- Petya: This ransomware attack also affected thousands of computers in 2017. It was spread through malicious email attachments and, like WannaCry, exploited a vulnerability in the Windows operating system.
- Cryptolocker: This ransomware was first discovered in 2013 and was one of the first examples of ransomware to gain widespread attention. It infected computers through malicious email attachments and encrypted the victim’s files, demanding payment in exchange for the decryption key.
- Ryuk: Ryuk is ransomware that has been used in targeted attacks against organizations. It encrypts files and demands a large ransom payment in exchange for the decryption key.
- Locky: It is one of the most widespread ransomware, which encrypts files and demands payment in Bitcoin. It is often delivered via spam emails with malicious attachments.
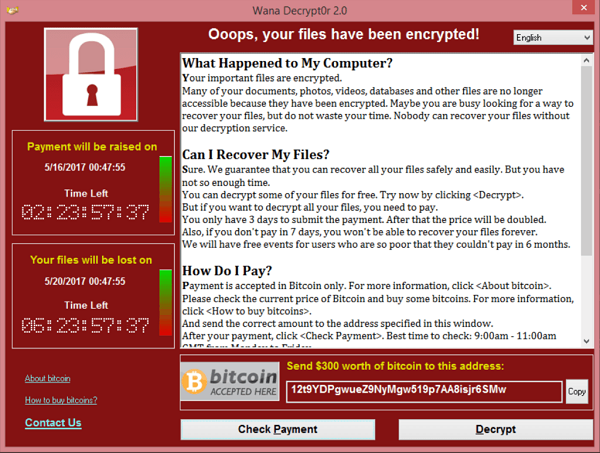
These are some examples, but new strains of ransomware are constantly being developed and used in attacks, so it’s important to stay informed and take steps to protect yourself.
Ransomware Protection
Protecting against ransomware requires a multi-layered approach that focuses on both prevention and readiness to respond.
- Regular software and operating system updates
- Implementing antivirus and antimalware software
- Cybersecurity education
- Implementing strong network security
- Regular and automatic data backups
- Cyber insurance policy
Ensuring that all systems and software are regularly updated is a good first line of defense. This includes operating systems, applications, and firmware on devices. Updates often include patches for security vulnerabilities that could be exploited by ransomware.
Implementing robust security solutions is essential. These solutions should include advanced antivirus and anti-malware software, which can detect and block ransomware attacks. Next-generation antivirus systems that utilize machine learning can be particularly effective in identifying and stopping ransomware.
The cost of ransomware damage was expected to exceed $20 billion globally.
Educating users plays a crucial role. Ransomware often infiltrates systems through phishing emails or malicious websites. Training users to recognize and avoid these threats can significantly reduce the risk. Regular security awareness training and simulated phishing exercises help reinforce good practices.
Implementing strong network security measures is also vital. This includes using firewalls to block unauthorized access and segmenting networks to limit the spread of ransomware if it penetrates the network. Intrusion detection and prevention systems (IDPS) can also be used to monitor network traffic for signs of suspicious activity.
Regularly backing up data is a critical defense against ransomware. Backups should be performed frequently and should be stored offline or in a separate cloud environment. This ensures that in the event of a ransomware attack, data can be restored without paying the ransom.
Using access controls effectively can limit the potential impact of ransomware. Implementing the principle of least privilege ensures that users have only the access necessary for their role. This limits the potential spread of ransomware through networked systems.
Monitoring systems and networks continuously allows for the early detection of ransomware activity. This involves not just automated monitoring tools but also having a team ready to respond to anomalies. The faster an intrusion is detected, the quicker it can be contained.
Having an incident response plan in place is crucial. This plan should outline the steps to take in the event of a ransomware attack, including isolation of infected systems, communication strategies, and steps for data recovery. Regularly testing and updating this plan ensures that it will be effective when needed.
Considering cyber insurance can provide additional protection. This insurance can help cover the costs associated with a ransomware attack, including recovery and legal fees. However, it’s important to understand what is covered under the policy and ensure that it aligns with the specific risks and needs of the organization.
Ransomware Delivery Methods
Ransomware delivery often employs several sophisticated techniques to infiltrate systems.
- Phishing Emails
- Software Vulnerabilities
- Drive-By Downloading via Compromised Websites
- Remote Desktop Protocol via Brute Force Attacks
- Malvertising
- Disguised File Sharing Files
- Social Engineering
Phishing emails are a common method. These emails contain malicious attachments or links that, when opened or clicked, execute the ransomware. The emails are usually crafted to look legitimate, tricking the user into taking the bait.
Exploiting vulnerabilities in software provides another avenue for ransomware delivery. Attackers identify weaknesses in commonly used software and design ransomware to take advantage of these flaws. Once an unpatched vulnerability is exploited, the ransomware can install itself without user interaction.
Drive-by downloading is a technique where ransomware is automatically downloaded when a user unknowingly visits a compromised website. This method often exploits vulnerabilities in web browsers or browser plugins.
Remote Desktop Protocol (RDP) is a frequent target for attackers. By using brute-force attacks or stolen credentials, attackers gain access to an organization’s network and manually install ransomware.

Malvertising involves embedding malicious code in online advertisements. When users click on these ads, the code redirects them to malicious sites or directly downloads ransomware onto their systems.
File-sharing networks are also a common method for spreading ransomware. Files disguised as legitimate software or media contain ransomware, which is activated once the file is downloaded and opened by the user.
Social engineering tactics extend beyond phishing emails. Attackers might use phone calls or other communication methods to trick users into enabling macros in documents, which then download ransomware.
Supply chain attacks represent a more sophisticated method. Attackers compromise a trusted piece of software or a vendor and use this as a conduit to distribute ransomware to the software’s users.
Attackers sometimes use a combination of these methods to increase their chances of successful delivery. For instance, a phishing email might lead to a website that exploits browser vulnerabilities, or a malvertising campaign might be used to direct users to a file-sharing site hosting malicious downloads.
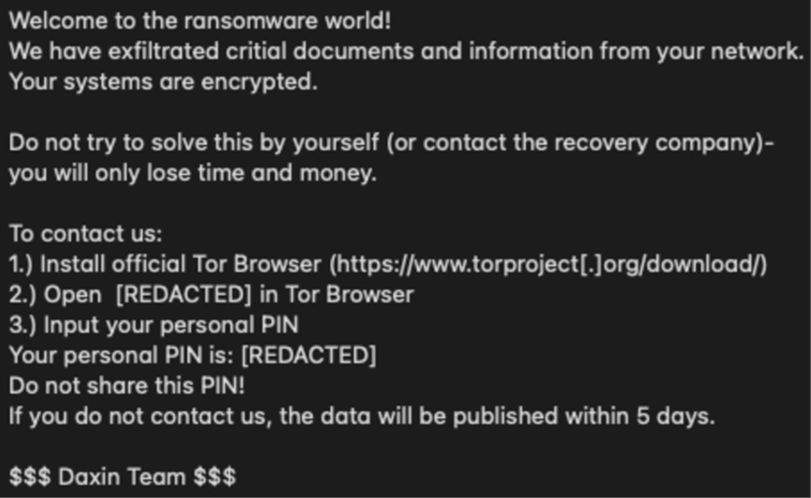
Should You Ever Pay a Ransomware Ransom?
Paying a ransom to ransomware attackers is not a guaranteed solution and it also encourages them to continue their illegal activity. Instead, it is generally recommended that you do not pay the ransom, as there are other ways to recover from a ransomware attack.
Here are a few reasons why you should not pay a ransom:
- There is no guarantee that the attackers will provide the decryption key: Even if you pay the ransom, there is no guarantee that the attackers will provide the decryption key or that the key will work.
- Paying the ransom may encourage more attacks: If attackers see that they can make money from their attacks, they will be more likely to continue launching similar attacks in the future.
- It might be illegal: Depending on the laws of your country, paying a ransom might be considered illegal and could lead to prosecution
- Alternatives: There are other ways to recover from a ransomware attack, such as restoring from a backup or seeking professional help from a cybersecurity expert.
In 2021, CNA Financial, an insurance company, paid a record $40 million to resolve a ransomware attack.
It’s important to remember that the best defense against ransomware is to prevent an attack from happening in the first place by implementing security measures and being vigilant. If you are infected and unable to recover, it’s best to take help from a professional cybersecurity expert.
2025 Data Sources
- https://www.ftc.gov/business-guidance/small-businesses/cybersecurity/ransomware
- https://www.cisa.gov/stopransomware
- https://www.secretservice.gov/
investigation/ransomware - https://www.fbi.gov/file-repository/ransomware-prevention-and-response-for-cisos.pdf/view
- https://www.whitehouse.gov/briefing-room/statements-releases/2021/10/13/fact-sheet-ongoing-public-u-s-efforts-to-counter-ransomware/