A whaling attack is a specific type of phishing attack that is targeted towards senior executives, CEOs, CFOs, or other high-profile individuals within an organization. These people are referred to as the “big fish” or “whales,” hence the name.
The goal of the attacker in a whaling attack is usually to trick the target into revealing sensitive information, such as login credentials or financial information, or to perform a certain action, such as making a wire transfer to a fraudulent account.
Whaling attacks are typically more sophisticated than standard phishing attacks. The phishing emails used in these attacks are often personalized and highly tailored to the target. They may involve extensive social engineering techniques, including using information about the target’s interests, job, or personal life to make the phishing email seem more legitimate.
Like other forms of phishing, whaling can be mitigated through a combination of technical security measures, user education, and the establishment of policies and procedures for handling sensitive information and requests.
Whaling vs Spear Phishing
Whaling cyberattacks and spear phishing are both highly targeted forms of phishing, but they differ significantly in their targets and methodologies.
Whaling attacks specifically target high-ranking individuals within an organization, such as CEOs, CFOs, or other senior executives. The term “whaling” is derived from the notion that these high-value targets are the “big fish” of the organization. These attacks are meticulously crafted to appear as legitimate as possible, often involving personalized emails that mimic the tone, style, and type of communication that the target would expect to receive. Whaling attempts might involve requests for sensitive financial information, wire transfers, or confidential employee data, leveraging the authority of the executive being impersonated to bypass normal security protocols.
Spear phishing, on the other hand, while also highly targeted, is not necessarily aimed at the highest-ranking individuals within an organization. Instead, spear phishing targets are selected based on their access to the desired information or systems, regardless of their position on the corporate ladder. These attacks are also personalized but can range from targeting mid-level management to technical staff, depending on what the attackers are after. Spear phishing messages are designed to trick the recipient into revealing passwords, downloading malware, or facilitating unauthorized access to secure systems, but they do not exclusively mimic the identity of top executives as whaling attacks do.
The key difference lies in the specificity and level of personalization of the attack, as well as the perceived value of the target to the attacker. Whaling seeks to exploit the high-level authority and access of top executives, while spear phishing exploits the specific access or information held by targeted individuals within the organization. Both require a deep understanding of the target and their organization, often leveraging information gleaned from social media, corporate websites, or previous data breaches to craft convincing and deceptive messages.
| Aspect | Whaling Cyberattack | Spear Phishing Cyberattack |
|---|---|---|
| Target | High-ranking individuals such as CEOs, CFOs, or senior executives. | Selected individuals based on their access to desired information or systems, regardless of their position. |
| Objective | Leverage authority of high-value targets to request sensitive information or financial transfers. | Trick recipients into revealing passwords, downloading malware, or unauthorized system access. |
| Methodology | Meticulously crafted, highly personalized emails mimicking legitimate communication styles and requests. | Personalized emails designed to exploit specific access or information, not necessarily mimicking top executives. |
| Personalization | Extremely high, often involving detailed knowledge about the target’s role, activities, and communication habits. | High, but focused on the individual’s access or role within the organization rather than impersonating top executives. |
| Defense | Combination of technical security measures, vigilant email practices, and continuous education on cyber threats. | |
What are the Signs of a Whaling Attack?
Whaling attacks can be sophisticated and highly targeted, which can make them harder to spot than a typical phishing attack. However, here are some signs that could indicate a possible whaling attack:
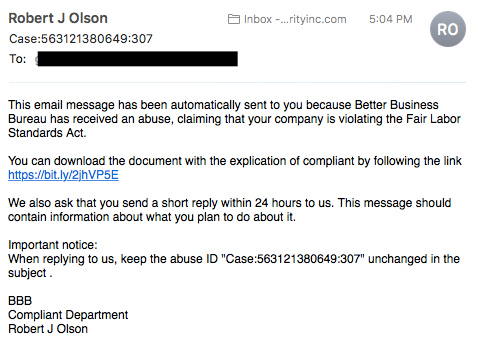
- Unexpected Emails: You’ve received an email that you weren’t expecting. This could be from a higher-up within your company, from a known vendor, or even from a governmental agency.
- Request for Sensitive Information or Urgent Action: The email may ask you to reveal sensitive data, such as usernames, passwords, financial details, or company secrets. It might also pressure you to perform an urgent task, like making a wire transfer or authorizing a payment.
- High-Level Sender: In a whaling attack, the email often appears to come from someone high up in the organization, such as a CEO, CFO, or another executive.
- Email Address and Domain: Although the name displayed in the email may look legitimate, always check the email address itself. Attackers often use email addresses that look very similar to the legitimate ones but may have subtle differences, such as a misspelling or a different domain.
- Grammar and Spelling Mistakes: Even though whaling attacks are typically more sophisticated than general phishing attacks, they might still contain grammatical errors or spelling mistakes, particularly if the attackers are not fluent in the language they’re using.
- Unusual Email Content or Tone: If the email’s content or tone doesn’t match what you’d expect from the supposed sender, be cautious. For example, if an email purportedly from your CEO includes personal details they wouldn’t typically share or uses an unfamiliar tone or language, it may be a whaling attempt.
- Non-standard URLs: Any links included in the email may lead to non-standard or unfamiliar URLs. Hover your cursor over the link to preview the URL before clicking.
- Attachments: Be suspicious of any unexpected email attachments, particularly if they come from an unexpected source. These can contain malware.
- Mismatched or Poorly Formatted Email Signature: The email signature may be inconsistent with the standard company signature, poorly formatted, or contain unusual information.
The absence of common phishing indicators, like poor spelling and grammar, makes these attacks harder to detect. Instead, attackers invest time in crafting convincing messages, possibly including the executive’s specific interests or activities gleaned from social media or corporate websites to enhance credibility.
Some key indicators of whaling cyber attacks include highly personalized communication that appears to originate from a trusted source, often mimicking the email format, language, and tone used within the targeted organization. These emails might request the transfer of funds, sensitive information, or access credentials, leveraging the authority of the executive being impersonated.
Another sign is the urgency and confidentiality stressed in the message, pressuring the recipient to act swiftly and bypass usual security protocols or verification processes. Whaling emails may exploit current corporate events, such as mergers, acquisitions, or financial reporting periods, to increase their believability.
Whaling attacks may involve sophisticated techniques such as domain spoofing or email spoofing, where the attacker’s email address closely mimics a legitimate one, with minor alterations detectable only upon careful inspection. Links within the email, supposedly leading to legitimate websites, may instead direct the recipient to malicious sites designed to harvest login credentials or install malware on the victim’s device. This malware can range from keyloggers for capturing keystrokes to ransomware or spyware that gives attackers access to the victim’s network.
How to Protect Against Whaling Attacks
Protecting against whaling attacks requires a combination of technical defenses, policy measures, and user awareness. Here are some ways to protect your organization from these types of attacks:
- Education and Training: Staff, and especially executives, should be trained to recognize the signs of a whaling attack. They should be aware of the tactics used by attackers and be cautious about unexpected requests for sensitive information or unusual transactions.
- Email Filtering and Monitoring: Use email filtering software to scan incoming emails for signs of phishing or whaling. This can help identify potentially dangerous emails before they reach the intended recipients.
- Multi-Factor Authentication (MFA): Implementing MFA can add an extra layer of security, making it more difficult for attackers to gain access to accounts even if they manage to obtain login credentials.
- Regularly Update and Patch Systems: Ensure that all systems are regularly updated and patched to fix potential vulnerabilities that could be exploited by attackers.
- Review and Update Policies: Have clear policies in place for financial transactions and handling sensitive information. This can include measures such as requiring in-person or phone confirmation for certain actions, or having a multi-person approval process for high-value transactions.
- Regular Backups: Regularly back up important data and ensure that it can be restored easily. This can help mitigate the damage if an attack does occur.
- Use Anti-Phishing Tools: Many web browsers and email clients offer anti-phishing features that can provide some level of protection against these attacks.
- Secure your email systems: Implement DMARC (Domain-based Message Authentication, Reporting & Conformance) which helps protect email senders and recipients from spoofing, and adds an additional layer of protection against whaling.
- Incident Response Plan: Have a well-defined incident response plan in place. If an attack does occur, this can help minimize the damage and ensure a quick recovery.
Protecting against whaling cyberattacks requires a multifaceted approach that combines technical safeguards, organizational policies, and continuous education.
Implementing advanced email security solutions like DMARC (Domain-based Message Authentication, Reporting, and Conformance), SPF (Sender Policy Framework), and DKIM (DomainKeys Identified Mail) helps authenticate emails and prevents spoofing, making it harder for attackers to impersonate high-ranking officials within an organization.
Deploying endpoint security measures, including antivirus software, anti-malware solutions, and intrusion detection systems, can protect individual devices and the network at large from the malware that might be distributed via whaling attacks.
Encryption of sensitive data, both at rest and in transit, ensures that even if attackers manage to intercept communications, the information remains unreadable and useless to them. Implementing strong password policies and multi-factor authentication adds another layer of security, making it more difficult for attackers to gain unauthorized access to corporate systems and sensitive information.
Regular security audits and penetration testing can identify vulnerabilities within the organization’s IT infrastructure that could be exploited in a whaling attack. Addressing these vulnerabilities promptly reduces the attack surface available to cybercriminals.
Education and training programs tailored for executives and their assistants are crucial. These programs should focus on the specifics of whaling attacks, including how to recognize and respond to suspicious emails, the importance of verifying unusual requests through alternate communication channels, and the risks associated with sharing too much personal or corporate information on social media platforms.
Creating a culture of security within the organization encourages employees at all levels to be vigilant and to question anomalies, reducing the chances of successful deception. Establishing clear protocols for the handling of financial transactions and sensitive information requests ensures that such actions are only taken following proper verification and approval, regardless of the apparent urgency or authority of the request.
2025 Data Sources