Spear phishing is a targeted form of phishing in which fraudulent emails, text messages, or other forms of communication are sent from what appears to be a known or trusted sender to induce targeted individuals to reveal confidential information.
The goal of a spear phishing attack is often to steal sensitive data, such as login credentials or credit card information, or to install malware on the target’s machine. Unlike a phishing attack, which is more broadly targeted, spear phishing attacks are carefully personalized to their targets. The attacker may use personal information about the target that has been collected from a variety of sources to make the fraudulent message seem more legitimate.
The name “spear phishing” derives from the fact that the attacker is “spear” targeting a specific individual or organization, rather than casting a wide “net” like in a standard phishing attack. These attacks can be particularly dangerous because of their tailored nature, which can make them more difficult to detect than standard phishing attempts.
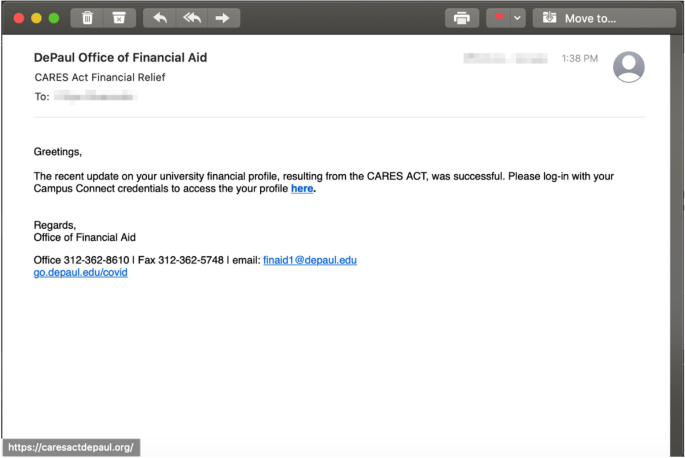
Phishing vs Spear Phishing
Phishing and spear phishing are both forms of social engineering attacks designed to deceive individuals into divulging sensitive information, but they differ significantly in their approach and target specificity.
Phishing is a broader strategy that casts a wide net, targeting large numbers of people with the hope that some will bite. These attacks are usually less personalized, often taking the form of generic emails that purport to be from reputable organizations, such as banks or social media platforms, requesting the recipient to update their information or confirm their login details. The emails are sent to a vast audience without regard for the individual’s specific relationship with the supposed sender.
Spear phishing, by contrast, is highly targeted. Attackers spend time gathering information about their victims to craft messages that are much more personalized and convincing. These attacks might leverage knowledge of the individual’s job position, workplace, interests, or personal connections, making the fraudulent communication seem legitimate. The goal is to trick the specific individual into performing an action, such as clicking on a malicious link, downloading an infected attachment, or providing confidential information. Spear phishing requires more effort and research on the part of the attacker but tends to have a higher success rate due to its personalized nature.
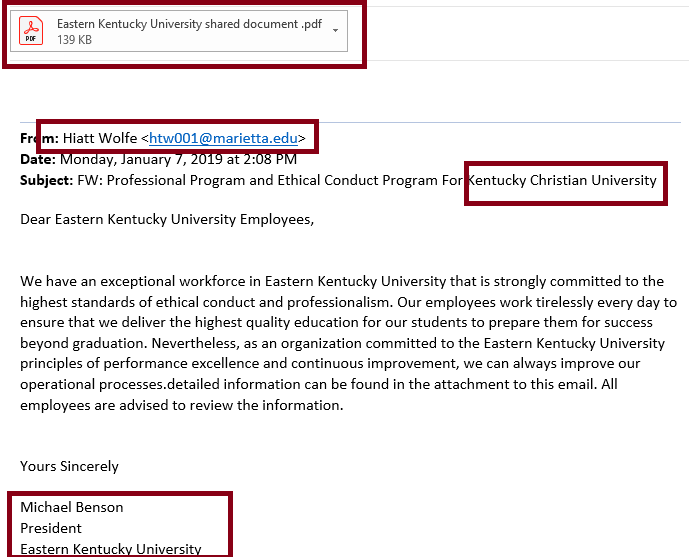
Spear phishing attacks may also employ more sophisticated techniques to bypass security measures. For instance, attackers might use social engineering to gather enough information to answer security questions or to craft emails that can bypass spam filters and other email security measures. In contrast, generic phishing attempts are often easier to detect and block due to their broad, impersonal nature and the use of easily identifiable scam tactics.
Phishing vs. Spear Phishing Comparison
| Aspect | Phishing | Spear Phishing |
|---|---|---|
| Targeting | Broad, targeting a large number of individuals | Highly targeted, focusing on specific individuals or organizations |
| Personalization | Generic messages with little to no personalization | Highly personalized messages based on the victim’s personal information |
| Technique | Uses generic emails that purport to be from reputable organizations | Employs sophisticated techniques, including detailed knowledge of the target |
| Success Rate | Lower success rate due to broad targeting | Higher success rate due to personalized approach |
| Defensive Strategies | Focuses on broader filtering and detection mechanisms | Requires nuanced approaches like advanced threat detection |
Signs of Spear Phishing
Spear phishing attempts can often be sophisticated and difficult to spot due to their personalized nature. However, here are some common signs to watch for:
- Urgency: The message often creates a sense of urgency or panic to trick the victim into responding without thinking. This could involve a claim that your account will be closed, your access revoked, or an important deadline missed if you don’t respond immediately.
- Requests for Personal or Financial Information: One of the most obvious red flags is if the email asks for sensitive data, such as passwords, credit card numbers, or bank account information. Legitimate organizations usually don’t ask for this information via email.
- Mismatched Email Addresses: Check the sender’s email address. It might look similar to the real one, but there might be slight alterations, like extra characters or a different domain.
- Poor Grammar and Spelling: While this isn’t always the case, especially with sophisticated attacks, phishing emails may contain poor grammar, typos, and spelling mistakes.
- Unexpected Attachments or Links: If you receive an email with an unexpected attachment or link, be very cautious. The attachment could contain malware, or the link might direct you to a phishing website designed to steal your information.
- Generic Greetings: Although spear phishing attacks are personalized, some may still use generic greetings, such as “Dear valued customer” or “Dear account holder”.
- Spoofed Hyperlinks and Domains: Hover over any links before clicking them to check the URL. In a phishing email, the link text may look legitimate, but the actual URL might lead to a different site. Also, check for subtle misspellings in the domain name of the website you’re directed to.
- Inconsistencies in Email Designs: Spear phishing emails may attempt to mimic official logos, colors, or company email designs, but there might be slight inconsistencies or low-quality elements.
One key indicator of spear phishing is the email or message’s personalized nature. Attackers often use detailed information about the target, such as their name, position, and specific interests, to make the communication seem legitimate. This information can be gathered from social media profiles, company websites, or other public sources.
Another sign is the presence of urgent or threatening language designed to provoke immediate action. The message may claim that the recipient’s account has been compromised or that they need to verify their information promptly to avoid negative consequences. This tactic plays on the target’s fear and urgency to bypass rational judgment.

Emails or messages with slight inconsistencies in the sender’s address or domain name also raise red flags. Spear phishers may use addresses that closely mimic legitimate ones, with subtle differences that can be easily overlooked, such as misspellings or additional characters.
Requests for sensitive information, such as passwords, financial details, or personal identification numbers, are a hallmark of spear phishing. Legitimate organizations typically do not ask for this type of information via email.
Attachments or links within the message that seems out of context or unexpected should be treated with suspicion. These could contain malware designed to compromise the recipient’s system or lead to phishing websites that capture entered information.
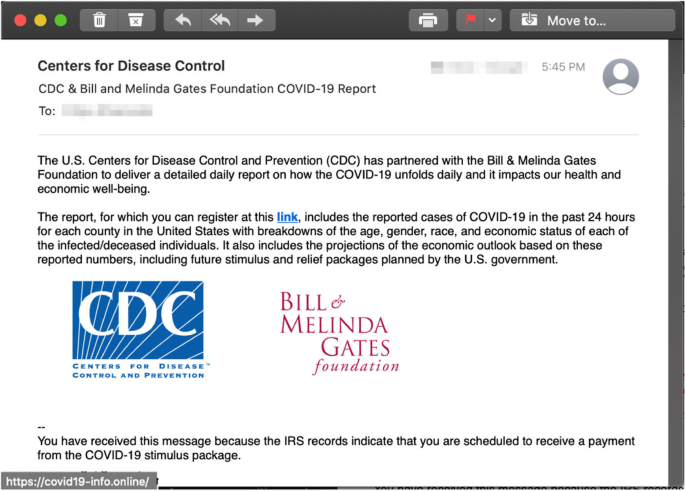
Poor grammar or spelling, while less common in sophisticated spear phishing attempts, can still be a telltale sign. However, many attackers now use professional-level language and formatting, making this criterion less reliable as a sole indicator.
It’s important to note that not all spear phishing emails will have these signs. Attackers are always refining their strategies to seem more legitimate. Always be cautious when opening emails, even if they appear to be from someone you trust. If something seems suspicious, contact the person or organization directly via a known contact method (like the phone number listed on their official website) to verify the communication.
Protecting Against Spear Phishing
Protecting yourself from spear phishing attacks requires a combination of good security practices and a healthy dose of skepticism. Here are some steps to take:
- Education and Awareness: The first step in protection is understanding what spear phishing is, how it works, and the common signs of an attack. This knowledge can help you spot and avoid malicious emails.
- Verify the Source: If you receive an unexpected email asking for sensitive information, don’t reply or click on any links. Instead, contact the person or organization directly using a phone number or email address that you know is legitimate to verify the request.
- Use Two-Factor Authentication (2FA): 2FA adds an additional layer of security to your online accounts by requiring two forms of verification before allowing access to an account. It’s not infallible, but it can provide significant protection.
- Be Careful With Personal Information: The less personal information you have available online, the less an attacker can use against you in a spear phishing attempt. Be thoughtful about what you post on social media and other public platforms.
- Keep Software and Systems Updated: Regularly update your operating systems and applications. Many updates include patches for security vulnerabilities that could be exploited by attackers.
- Use Security Software: A robust security solution can detect and quarantine phishing emails, provide a warning before you visit dangerous sites, and prevent malware attacks.
- Check Email Addresses and URLs Carefully: Spear phishing often involves slightly altered email addresses and URLs. Always check these carefully to make sure they are legitimate.
- Don’t Click on Suspicious Links or Attachments: Be wary of unexpected links or attachments, even if they appear to come from a trusted source.
- Regularly Check Your Accounts: Regularly check your financial and online accounts for any suspicious activity. If you notice anything strange, report it immediately.
- Use Strong, Unique Passwords: Avoid using the same password for multiple accounts. If one account is compromised, the others will still be safe. Consider using a password manager to handle complex passwords.
Remember, no method is foolproof, and attackers are always finding new ways to exploit security measures. Staying informed about the latest phishing techniques and maintaining good online security habits is the best way to protect yourself.
Spear Phishing Protection for Businesses
Protecting against spear phishing attacks on businesses requires a multifaceted approach that combines technology, education, and policy enforcement. Implementing advanced email filtering solutions is a critical first step. These systems use algorithms to analyze email content, headers, and sender reputation to identify and quarantine phishing attempts before they reach the user’s inbox. Employing domain-based message authentication, reporting, and conformance (DMARC) policies can also help in verifying the authenticity of the emails, reducing the chances of spoofed messages getting through.
Regular training sessions for employees are essential to raise awareness about spear phishing tactics and the importance of scrutinizing emails. Simulated phishing exercises can test employees’ vigilance and reinforce training by providing real-world scenarios in a controlled environment. Encouraging a culture of skepticism and verification can significantly reduce the risk of successful attacks. Employees should be trained to verify the identity of the sender through independent channels before responding to requests for sensitive information or clicking on links.
88% of organizations face spear phishing attacks.
Implementing strong access control policies and using multifactor authentication (MFA) adds another layer of security. Even if credentials are compromised, MFA can prevent unauthorized access. Ensuring that systems and software are kept up to date with the latest security patches reduces vulnerabilities that could be exploited by malware delivered through spear phishing.
Data loss prevention (DLP) tools monitor and control data transfers, preventing sensitive information from being leaked or sent outside the network without authorization. Encryption of sensitive data at rest and in transit ensures that intercepted data cannot be easily exploited by attackers.
Creating an incident response plan that includes procedures for responding to suspected spear phishing attempts ensures a swift and coordinated reaction to potential breaches. This plan should include steps for isolating affected systems, changing passwords, and notifying affected parties.
Fostering an organizational culture that promotes security as a shared responsibility can help in creating an environment where employees feel empowered to report suspicious activities without fear of repercussion. This collective vigilance can be one of the most effective defenses against spear phishing.
Spear Phishing and the Risk of Identity Theft
Spear phishing can indeed lead to identity theft. In fact, it’s one of the primary ways identity thieves gain access to the personal information they need to commit their crimes.
When a victim falls for a spear phishing scam, they may inadvertently provide the attacker with sensitive information such as social security numbers, bank account details, credit card numbers, or passwords to various accounts. With this information, the attacker can steal the victim’s identity, potentially opening new lines of credit, making purchases, or even committing crimes in the victim’s name.
Spear phishing attacks make up 0.1% of all email-based attacks but are responsible for 66% of breaches.
This is why it’s so important to be vigilant when receiving any communication that requests personal or financial information. Even if the message appears to be from a known and trusted source, it’s always best to independently verify the request through a different means of communication before providing any sensitive information.
2025 Data Sources
- https://archives.fbi.gov/archives/news/
stories/2009/april/spearphishing_040109 - https://www.dni.gov/files/NCSC/documents/
campaign/Counterintelligence_Tips_
Spearphishing.pdf - https://csrc.nist.gov/glossary/term/
spear_phishing - https://www.nyu.edu/life/information-technology/about-nyu-it/nyu-it-news/the-download/the-download-features/phishing-spear-phishing-whaling.html
- https://consumer.ftc.gov/consumer-alerts/2018/10/spear-phishing-scammers-want-more-you