Trojan viruses are a type of malware that disguises itself as a legitimate software program or file. They can be delivered through a variety of methods, such as email attachments, downloads from untrusted websites, or even through social engineering tactics such as phishing scams. Once the Trojan is installed on the target computer or device, it can perform a wide range of malicious actions, such as stealing sensitive information, installing additional malware, or even taking control of the computer remotely.
How do Trojan Viruses Work?
Trojan viruses are malicious pieces of software that masquerade as legitimate applications. Unlike other viruses or worms, they do not replicate themselves but they create a backdoor for malicious users to control the infected computer.
The sophistication of Trojan viruses lies in their disguise. They often appear as useful software, enticing users to install them. Upon execution, they perform the expected functions to avoid immediate suspicion, but in the background, they deploy malicious activities. These activities can range from logging keystrokes to capture sensitive information like passwords and financial data, to installing other malware or ransomware, and even creating a part of a botnet for coordinated attacks.
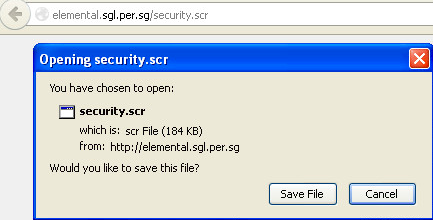
Trojans are typically spread through social engineering tactics. Phishing emails, fake advertisements, or websites trick users into downloading and installing the malware. Once installed, the Trojan virus communicates with a command and control (C&C) server operated by the attacker. This server can send commands to the infected computer, allowing the attacker to steal data, monitor user actions, or distribute more malware.
Trojan viruses can vary widely. Some use polymorphic code to alter their appearance and evade detection by antivirus software, while others exploit zero-day vulnerabilities, which are security holes in software that are unknown to the vendor. This makes them particularly dangerous and difficult to defend against.
For persistence, Trojans often modify system files and registry keys. This ensures they are executed at every system startup. They may also disable security measures, such as antivirus software and firewalls, making the system more vulnerable to further attacks.
Trojans Account for 58% of All Malware.
Network traffic generated by Trojan viruses is often encrypted, making it harder for network monitoring tools to detect and block malicious activities. Moreover, by using techniques like fast flux, where the domain names associated with the C&C servers change rapidly, Trojans can keep the communication with attackers hidden and persistent.
The impact of a Trojan virus can be devastating. From a personal perspective, it can lead to identity theft, financial loss, and unauthorized access to private communications. On a corporate level, it can result in data breaches, espionage, and significant financial and reputational damage.
List of Well-Known Trojan Viruses
Several trojans have made headlines over the years due to their destructive capabilities, sophisticated mechanisms, or widespread impact. Here is a list of some well-known trojans:
- Zeus (Zbot): This trojan is known for its ability to perform man-in-the-browser attacks and keystroke logging. It has been widely used to steal banking information by capturing login credentials.
- CryptoLocker: A ransomware trojan that gained notoriety for encrypting the victim’s files and demanding ransom payments for the decryption key. It spread primarily through email attachments and infected millions of computers worldwide.
- Emotet: Originally identified as a banking trojan, Emotet evolved into a sophisticated malware delivery service. It could spread itself through networks and load other malware onto the infected systems, including other banking trojans and ransomware.
- Dridex: A banking trojan that targets Windows users, primarily through phishing emails. Dridex is known for stealing banking credentials by injecting malicious code into web pages.
- Back Orifice: Created by the hacker group Cult of the Dead Cow, Back Orifice allows remote control of a Windows system and was often used for malicious purposes, despite being presented as a tool to demonstrate Windows vulnerabilities.
- DarkTequila: A sophisticated trojan targeting Latin American users, known for stealing banking information, corporate data, and personal credentials offline, thereby avoiding detection by network-based antivirus solutions.
- RAT (Remote Access Trojan): This category includes various trojans such as Gh0st RAT and BlackShades, which allow attackers to control infected computers remotely, often used for espionage, stealing information, or installing more malware.
- Pegasus: Although technically classified as spyware, Pegasus has trojan-like capabilities. It is a highly sophisticated tool used for surveillance, capable of infecting smartphones to spy on calls, messages, and use the camera and microphone.
- LockerGoga: Known for its impact on industrial and corporate networks, this ransomware trojan encrypts files and demands a ransom. It has caused significant operational disruptions by targeting industrial and manufacturing firms.
- TrickBot: Initially a banking trojan, TrickBot has evolved to perform a wide range of malicious activities, including credential theft, data exfiltration, and delivering ransomware. It is known for its modular architecture, allowing it to add new capabilities easily.
Devices and Operating Systems Affected by Trojans
Trojan viruses are not limited by device type or operating system, making virtually any computer or mobile device susceptible to infection.
Windows operating systems have historically been prime targets due to their widespread use and the valuable data they often hold. However, macOS is not immune; while it’s less frequently targeted, there have been increasing instances of Trojans and other malware designed to infiltrate Mac systems. Linux, often praised for its security features, also faces threats from Trojans, particularly those targeting servers or systems running popular Linux distributions.
Android operating systems are particularly vulnerable to Trojan viruses. The open nature of the Android ecosystem, combined with the ability to install apps from third-party sources, increases the risk of Trojan infections. Although iOS devices, including iPhones and iPads, operate within a more controlled environment due to Apple’s stringent app review process and restricted system access, they are not entirely immune. Jailbroken iOS devices, which bypass Apple’s security restrictions to allow the installation of unauthorized apps, are especially at risk.
Internet of Things (IoT) devices, including smart home gadgets, wearables, and connected appliances, have emerged as new fronts in the battle against Trojans and other cyber threats. These devices often run on customized versions of popular operating systems like Linux, making them potential targets for attackers looking to exploit their generally weaker security measures for various malicious purposes, including gaining access to networks or conducting distributed denial-of-service (DDoS) attacks.
Enterprise systems and servers, regardless of whether they run Windows Server, Linux, or another operating system, can also be compromised by Trojans designed to steal data, spy on business operations, or serve as a foothold for further network infiltration.
Trojan Virus Protection Methods
The following are some steps you can take to protect yourself against Trojan viruses:
- Keep your operating system and software up-to-date: Regularly update your operating system and software to ensure that you have the latest security patches and updates. This can help prevent Trojans from exploiting vulnerabilities in your system.
- Use antivirus software: Install and use reputable antivirus software on your computer or device. Antivirus software can help detect and remove Trojans before they can cause harm.
- Be cautious of email attachments and downloads: Be wary of email attachments and downloads from untrusted sources. If you receive an email with an attachment or link that you were not expecting or from an unknown sender, do not open it.
- Use strong passwords: Use strong, unique passwords for all your accounts and change them regularly. This can help prevent Trojans from accessing your accounts and stealing your sensitive information. You can also securely store passwords with a password manager.
- Be cautious of social engineering tactics: Be wary of phishing scams and other social engineering tactics that are designed to trick you into revealing sensitive information or installing malware on your computer or device.
Ensuring that all software, especially the operating system and applications frequently targeted by attackers, like web browsers and email clients, are kept up to date with the latest security patches is crucial. These updates often fix vulnerabilities that could be exploited by Trojans.
Antivirus and anti-malware solutions play a key role in detecting and removing malicious software. These should be kept up to date with the latest virus definitions to recognize new threats. Employing a reputable security suite that includes real-time scanning, heuristic analysis to detect previously unknown viruses, and behavior monitoring can significantly reduce the risk of infection.
Firewalls, both software and hardware-based, help to block unauthorized access to a computer or network. Configuring firewall rules to restrict inbound and outbound connections to only those that are necessary for legitimate activities can limit the channels through which Trojans can communicate with attackers.
Email filters that block spam and phishing attempts reduce the chance of encountering malicious attachments and links that could harbor Trojans. Training users to recognize and report phishing attempts is equally important, as human error often leads to successful infections.
Using strong, unique passwords and changing them regularly can prevent unauthorized access even if a Trojan manages to capture sensitive information. Multi-factor authentication adds an additional layer of security by requiring a second form of verification beyond just a password.
Regularly backing up important data to an external drive or cloud storage that is not always connected to the network can mitigate the damage caused by Trojans, especially ransomware that encrypts files and demands payment for their release.
Network monitoring tools and intrusion detection systems can detect unusual network traffic and potentially unauthorized activities, indicating a Trojan infection. These tools can alert administrators to take immediate action to contain and eliminate the threat.
Educating users about the risks associated with downloading and installing software from unknown or untrusted sources is fundamental. Encouraging skepticism about unsolicited emails, even those that appear to be from legitimate sources, can prevent many Trojan infections.
Implementing application whitelisting, which allows only approved software to run, can prevent unauthorized applications, including Trojans, from executing. While this approach requires more management, it significantly enhances security.
What Should You Do if You Have a Trojan Virus?
If you suspect that your device may be infected with a Trojan virus, there are several steps you should take to address the issue:
- Run a full system scan: Use reputable antivirus software to run a full system scan on your device. The software should be able to detect and remove any Trojans or other malware that may be present.
- Disconnect from the internet: If you suspect that your device may be infected, disconnect it from the internet to prevent the Trojan from communicating with its command-and-control server or downloading additional malware.
- Change passwords: Change the passwords for all your accounts, especially those that may have been compromised, such as online banking or email accounts.
- Backup your data: Backup your important files and data to an external storage device, such as an external hard drive or cloud-based storage service, to prevent data loss in case of further damage to your device.
- Seek professional help: If you are unsure of how to remove the Trojan virus or if the damage is severe, consider seeking professional help from a reputable computer repair service or IT specialist.
If a Trojan virus infects your system, immediate action is required to minimize damage and prevent further infections. Disconnecting from the internet is the first step, stopping the Trojan from communicating with its command and control server, thereby halting any ongoing data theft or additional malicious downloads.
Running a full system scan using up-to-date antivirus and anti-malware software is crucial. These tools can detect and remove the Trojan along with any other malicious software that may have been installed. If the infection is severe, the software might not be able to remove it completely, or the system may become unstable after removal. In such cases, restoring from a clean, recent backup can ensure that all traces of the malware are eliminated. However, ensure the backup is clean and was created before the infection occurred.
In the absence of a clean backup or if the backup is too outdated, considering a clean reinstall of the operating system may be necessary. While this measure is drastic, it guarantees the removal of the Trojan and any other malware from the system. Before doing so, backing up important files is important, but only after thoroughly scanning them for malware to prevent re-infection.
Changing all online passwords and monitoring financial transactions for signs of unauthorized activity is advisable, especially if the Trojan could have captured sensitive information like usernames, passwords, or financial data. Implementing two-factor authentication on accounts adds an extra layer of security.
Updating all software, especially the operating system, browsers, and any applications that were vulnerabilities can prevent future infections. Patching these vulnerabilities reduces the risk of being exploited by other malware.
Reviewing and tightening security practices can prevent future infections. This includes educating users about the dangers of phishing emails, the importance of not downloading or opening attachments from unknown sources, and the necessity of regular software updates.
Implementing stronger network security measures, such as a more robust firewall and intrusion detection system, can help detect and prevent unauthorized access and malware infections.
Consulting with IT professionals or cybersecurity experts can provide additional insights into the specific Trojan’s behavior and advice on preventing future infections. They can also assist in enhancing the overall security posture of the individual or organization.
Engaging with professional cybersecurity services for a thorough security audit and ongoing monitoring can be a wise investment, especially for businesses, to identify vulnerabilities and implement best practices in cybersecurity.
Reporting the infection to relevant authorities or cybersecurity information sharing platforms can help others become aware of new threats and contribute to the collective defense against cyber threats.
Trojan Virus Removal
Removing a Trojan virus effectively involves several critical steps to ensure the malware is completely eradicated from your system and to prevent future infections:
- Isolate the Infected Device: Immediately disconnect the infected device from the internet and any network connections to prevent the spread of the virus and the theft of data.
- Enter Safe Mode: Restart the computer in Safe Mode, which loads only the essential programs and services. This step can prevent the Trojan from blocking your removal efforts.
- Update Your Antivirus Software: Ensure that your antivirus or anti-malware software is up to date with the latest virus definitions. If you don’t have security software installed, install it using a clean computer and then transfer it to the infected device using a USB drive.
- Run a Full System Scan: Perform a full system scan with the antivirus software to detect and remove the Trojan and any related malware. Be prepared to follow the software’s recommendations for dealing with any detected threats.
- Use a Malware Removal Tool: Consider using a specialized malware removal tool for an additional layer of scanning and removal capabilities, especially if the antivirus scan doesn’t resolve the issue.
- Manually Remove the Malware (if necessary): For advanced users, manual removal may be an option by identifying and deleting the malicious files and registry entries. This approach requires significant caution and understanding of the Windows operating system to avoid damaging the computer.
- Reset Your Passwords: After removing the Trojan, change all your passwords, especially if the malware had the capability to log keystrokes or steal password information.
- Patch Your Software: Update your operating system, browsers, and all installed software to the latest versions. This closes vulnerabilities that Trojans and other malware might exploit.
- Review and Tighten Security Settings: Adjust your computer and network security settings to enhance protection. Enable firewalls, adjust privacy settings, and ensure your software is set to update automatically.
- Educate Yourself and Others: Learn about common methods used to distribute Trojans, such as phishing emails and compromised websites, and educate others on these risks. Being cautious about downloads and email attachments can prevent many infections.
- Regular Backups: Maintain regular backups of your important data. If a Trojan or other malware compromises your system in the future, having backups will allow you to restore your files without paying ransoms or losing important information.
Removing a Trojan virus requires a systematic approach to ensure the malware is completely eradicated and the system is secured. Initiating the process by isolating the infected device from the network prevents the Trojan from sending data to attackers or downloading additional malware. This can be done by disconnecting the Ethernet cable or disabling the Wi-Fi.
Running a full system scan with updated antivirus and anti-malware software is the next critical step. These tools can identify and remove the Trojan along with any related malicious files and registry entries. It’s important to use reputable security software known for effectively detecting and removing malware.
In cases where the Trojan prevents the installation or updating of antivirus software, starting the computer in Safe Mode can be helpful. Safe Mode with Networking limits the number of running programs and services, potentially preventing the Trojan from blocking antivirus tools. From Safe Mode, installing, updating, and running a malware scan can be more effective.
Utilizing a malware removal tool specifically designed to target and remove Trojans and other malware types can provide an additional layer of cleaning. These tools often include features for repairing the damage to system files and settings caused by the Trojan.
Manually removing the Trojan is an option for experienced users who understand registry editing and system file management. This involves identifying and deleting malicious files and registry values based on their known characteristics. However, this method carries risks of accidentally deleting critical system files or registry entries, so it should be approached with caution.
Resetting all system passwords and credentials is essential after removing the Trojan, especially if there’s any possibility it was designed to steal personal information. This includes passwords for user accounts, online banking, email, and any other services accessed from the infected computer.
Updating the operating system, web browsers, and all installed software to their latest versions closes vulnerabilities that could be exploited by Trojans and other malware. Regularly applying patches and software updates is a key preventive measure against future infections.
Reviewing and adjusting security settings on the computer and network devices, including routers and firewalls, enhances protection against unauthorized access and malware. Enabling features like automatic updates, configuring firewalls to block unknown incoming connections, and setting up network encryption can significantly improve security.
Monitoring the system for signs of reinfection or other anomalies is important following a Trojan removal. Continuous vigilance helps in identifying potential threats early and taking prompt action to mitigate them.
Bottom Line
Trojan viruses are a serious threat that can cause significant harm to your computer or device. By following the above steps, you can help protect yourself against these malicious programs and stay safe online. Remember to always be cautious of suspicious emails, downloads, and social engineering tactics, and to keep your software and security measures up-to-date.
2025 Data Sources