Keylogging, also known as keystroke logging, is a method used by cybercriminals to gain unauthorized access to sensitive information. It involves the use of specialized software to record every keystroke made on a keyboard, including passwords, credit card numbers, and other confidential data.
The use of keyloggers is widespread in both personal and professional settings. Employers may use keyloggers to monitor the activities of their employees, while parents may use them to keep an eye on their children’s online activities. Unfortunately, keyloggers can also be used for malicious purposes, and cybercriminals have developed numerous ways to infect computers and steal sensitive information.
Types of Keyloggers
Keyloggers employed in cyberattacks are primarily software-based due to their stealthy nature and ease of distribution.
Kernel-Based Keyloggers
Kernel-based keyloggers are particularly formidable. They operate at the operating system’s kernel level, granting them near-unfettered access to the system’s processes and user keystrokes. Their deep integration into the system architecture makes them difficult to detect and remove.
API-Based Keyloggers
API-based keyloggers are also common in cyberattacks. These keyloggers hook into the system’s application programming interface (API) to monitor and record keyboard inputs across different applications. Their versatility in capturing keystrokes from a variety of applications makes them a preferred choice in broader surveillance operations.
Form Grabbing Keyloggers
Form Grabbing-based keyloggers are specifically tailored for financial and identity theft. They target web forms, capturing data as it’s entered, which is particularly useful for stealing login credentials, credit card information, and other personal data.
JavaScript Keyloggers
JavaScript keyloggers represent a more web-centric approach. By embedding malicious scripts in web pages, attackers can capture keystrokes in real-time as users interact with web forms. This method is particularly effective in phishing attacks and compromising online accounts.
Remote Access Trojans (RATs)
Remote Access Trojans (RATs) often come equipped with keylogger functionalities. These multifaceted malware tools provide attackers with remote control over infected systems, and the keylogging component is used to stealthily harvest user credentials and other sensitive information.
Memory-Scraping Keyloggers
Finally, memory-scraping keyloggers are emerging in sophisticated cyberattacks. These keyloggers scan the system’s memory to extract unencrypted keystroke data, bypassing conventional security measures that might detect more direct keylogging methods.
Each of these keylogger types is engineered to fit specific aspects of cyberattacks, whether it’s for widespread data harvesting, targeted espionage, or financial fraud. The choice of keylogger often reflects the attacker’s objectives, technical sophistication, and the intended target’s security environment.
How Keyloggers Are Used in Cyberattacks
Keyloggers in cyberattacks are tools of stealth and deception, used to covertly gather sensitive information from unsuspecting victims. These software programs, once installed on a target system, operate in the background, recording every keystroke made by the user. This data, which can include usernames, passwords, credit card numbers, and personal messages, is then silently transmitted to the attacker.
In targeted attacks, keyloggers are often deployed through spear-phishing campaigns. These carefully crafted emails trick recipients into executing malicious attachments or visiting compromised websites, leading to the installation of the keylogger. Once active, the keylogger begins its surveillance, capturing login credentials for various online services, which can then be used for unauthorized access, financial theft, or further penetration into a network.
Cybercriminals also use keyloggers in broader malware campaigns. Bundled within Trojan horses or other types of malware, keyloggers spread to a wide array of systems, indiscriminately collecting data from numerous victims. This data is then either used directly by the attackers or sold on the dark web for profit.
In more advanced scenarios, keyloggers are part of a larger toolkit in Remote Access Trojans (RATs). These RATs provide attackers with extensive control over infected machines, and the keylogging functionality is just one of many tools used to exploit, monitor, and extract data from the system.
Attackers also employ keyloggers in persistent threats against organizations. Here, the keylogger is just one element in a multi-stage attack, designed to maintain long-term access to sensitive systems and data. Infiltration often involves exploiting network vulnerabilities or social engineering tactics to install the keylogger, which then becomes a critical tool for gathering credentials needed to move laterally within the network, accessing increasingly sensitive and valuable information.
The effectiveness of keyloggers in cyberattacks hinges on their ability to remain undetected. Advanced keyloggers use various evasion techniques, like rootkit functionality, to hide their presence from antivirus programs and system monitoring tools. This stealth is crucial, allowing the keylogger to operate over extended periods, maximizing the amount of data captured and the potential damage inflicted.
Devices Susceptible to Keylogging Attacks
Virtually any device with input capabilities and internet connectivity can fall prey to keylogging cyberattacks. Computers, both desktops and laptops, are traditional targets due to their widespread use and the wealth of information they process. Windows operating systems, prevalent in both personal and corporate environments, are frequently targeted due to their large user base. MacOS and Linux systems are not immune; attacks on these platforms are on the rise as their popularity grows.
Smartphones and tablets, running on platforms like Android and iOS, have become increasingly susceptible. The ubiquity of mobile devices and the sensitive nature of the data they handle make them attractive targets for keyloggers. These devices are particularly vulnerable to app-based threats, where malicious applications masquerade as legitimate ones to capture keystrokes and other inputs.
In the corporate sector, servers and networked devices can also be compromised. While traditionally not the primary target for keyloggers, their role as repositories and conduits of sensitive information makes them valuable for prolonged espionage or data exfiltration activities.
Peripheral devices, like USB keyboards, can also be targeted by hardware-based keyloggers. These devices, when tampered with, can record keystrokes and store them or transmit them to an attacker.
Point-of-sale (POS) systems are another critical target. Often running on standard operating systems, they are vulnerable to the same types of keylogging software that affect PCs. For attackers, the payoff here is direct access to financial and personal data from card transactions.
IoT devices, though not a typical target for keylogging due to their limited input capabilities, should not be overlooked. As these devices become more sophisticated and interconnected, the potential for exploitation increases, particularly in scenarios where they interface with more traditional computing devices.
Gaming consoles and other entertainment devices, increasingly connected and featuring online capabilities, also present potential vulnerabilities. While less likely to be targeted for keylogging, their integration into home networks and their occasional use for web browsing or communication makes them a potential vector for attack.
Keylogging and Identity Theft
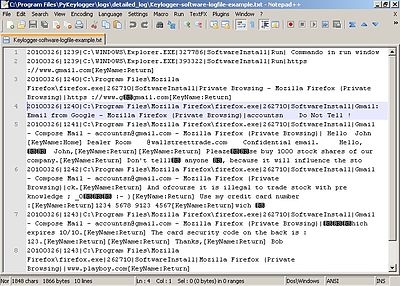
Keyloggers are a common tool used by cybercriminals in identity theft. By using a keylogger, a cybercriminal can capture all of the keystrokes made by the victim on their computer, including usernames, passwords, credit card numbers, and other sensitive information.
Once the keylogger has captured the victim’s information, it is typically transmitted back to the cybercriminal through a variety of methods, such as email or uploading the data to a remote server. The cybercriminal can then use this information to assume the victim’s identity and carry out fraudulent activities, such as opening new credit card accounts, taking out loans, or making unauthorized purchases.
One common way that keyloggers are used in identity theft is through phishing attacks. In a phishing attack, the cybercriminal sends an email to the victim that appears to be from a legitimate source, such as a bank or an online retailer. The email typically contains a link that, when clicked, installs the keylogger on the victim’s computer. The keylogger then captures the victim’s login credentials and other sensitive information, which the cybercriminal can use to steal the victim’s identity.
Another way that keyloggers are used in identity theft is through malware. Malware is a type of software that is designed to damage or disrupt computer systems. Some types of malware, such as trojans, are designed to install keyloggers on the victim’s computer without their knowledge. The keylogger then captures the victim’s sensitive information, which the cybercriminal can use to steal their identity.
How to Detect Keylogging
Detecting keyloggers in the realm of cyber security calls for a multifaceted approach, blending technical strategies with proactive monitoring. Antivirus and anti-malware programs are the first line of defense, equipped with signatures and heuristic analysis to identify and neutralize known keylogger strains. Sophisticated keyloggers often evade these traditional detection methods.
Behavior-based detection systems play a crucial role in identifying anomalous activities indicative of keylogger operations. These systems monitor for unusual system behavior, such as unfamiliar processes accessing keyboard APIs or transmitting data unexpectedly. This anomaly detection is particularly effective against custom or previously unknown keyloggers.
Network traffic analysis provides another avenue for detection. Keyloggers, to be effective, must transmit captured data. Monitoring outgoing network traffic for unusual patterns or destinations can flag potential keylogger activity. Encrypted traffic to unknown servers or frequent data transmissions to external IP addresses might indicate a compromise.
System and process monitoring tools delve deeper, examining running processes and their behaviors. Unrecognized or hidden processes, especially those exhibiting keyboard hooking behavior, warrant further investigation. Tools that monitor for rootkit-like behaviors can uncover keyloggers attempting to embed themselves deeply within the system.
Regular system audits and reviews are also vital. These include checking for unauthorized software installations, unexpected system configuration changes, and ensuring that security patches are up-to-date. Often, keyloggers are introduced through exploits in outdated software, so maintaining a robust patch management protocol is essential.
User education and awareness form the cornerstone of keylogger detection. Users trained to recognize phishing attempts and suspicious behaviors can prevent the installation of keyloggers in the first place. Vigilance in recognizing signs of system compromise, like slow performance or altered settings, can prompt early investigations, potentially unearthing hidden keyloggers.
Employing advanced security solutions like Endpoint Detection and Response (EDR) systems can significantly enhance keylogger detection capabilities. EDR systems provide continuous monitoring and response mechanisms, analyzing a wealth of data points to detect, isolate, and remediate threats like keyloggers in real-time.
How to Protect Against Keylogging
There are several ways to protect yourself from keyloggers. The first and most important is to be cautious when opening emails and clicking on links. Always verify the legitimacy of an email before clicking on any links or downloading any attachments.
Another effective way to protect yourself from keyloggers is to use a virtual keyboard. A virtual keyboard is a software program that allows you to enter keystrokes by clicking on a graphical representation of a keyboard on your screen. Since virtual keyboards use the mouse to input keystrokes, they are not vulnerable to keyloggers that record keystrokes on the physical keyboard.
Encryption is also an effective way to protect yourself from keyloggers. By encrypting your data, you can prevent cybercriminals from accessing your sensitive information even if they are able to record your keystrokes. This can be done by using encryption software to encrypt files or by using secure communication channels when transmitting sensitive data.
Bottom Line
Keylogging is a serious threat that can result in the theft of sensitive information. Cybercriminals use keyloggers to steal passwords, credit card numbers, and other confidential data. To protect yourself from keyloggers, it is important to be cautious when opening emails and clicking on links, keep your antivirus and antimalware software up to date, use a virtual keyboard, and encrypt your data. By taking these precautions, you can help ensure that your sensitive information remains safe and secure.
2025 Data Sources
- https://www.ncbi.nlm.nih.gov/pmc/articles/
PMC7928946/ - https://jolt.law.harvard.edu/digest/federal-and-state-wiretap-act-regulation-of-keyloggers-in-the-workplace
- https://csrc.nist.gov/glossary/term/
key_logger - https://www.cisa.gov/news-events/news/when-tech-vendors-make-important-logging-info-available-free-everyone-wins