Phishing is a type of online fraud in which attackers attempt to trick individuals into providing sensitive information, such as login credentials or financial information, by masquerading as a trustworthy entity in an electronic communication. This is typically done through email or instant messaging and often directs the victim to a fake website that appears legitimate but is actually controlled by the attacker.

Signs of a Phishing Attack
Phishing attacks often exhibit certain characteristics that can be identified by a vigilant observer.
- Discrepancies in email address
- Fear or urgency-based email content
- Suspicious links or attachments
- Spelling or grammatical errors
- Request for sensitive information
These attacks typically start with an email or message that appears to be from a legitimate source, such as a well-known company, a financial institution, or even a colleague or friend. However, upon closer inspection, the email address may show subtle discrepancies, like misspellings or incorrect domains that mimic the real ones.
The content of a phishing email usually creates a sense of urgency or fear, prompting the recipient to act quickly. This could be a warning about an unauthorized login attempt, a problem with an account, or a deadline for responding to an important request. This tactic is designed to provoke a quick reaction, bypassing rational judgment.
Phishing messages often contain links or attachments. The links might lead to fake login pages designed to harvest credentials. These pages are often well-crafted replicas of legitimate websites, but the URL might contain anomalies like a misspelled domain name or a domain that doesn’t match the supposed sender’s organization. Attachments in phishing emails could be disguised as routine documents but are often laden with malware.
Spelling and grammatical errors are more common in phishing emails compared to legitimate corporate communication. Although more sophisticated phishing campaigns can be flawlessly executed, many still contain language that doesn’t align with the supposed sender’s normal communication style.
Requests for sensitive information are a red flag. Legitimate organizations typically do not ask for passwords, social security numbers, or other sensitive personal information via email.
Sometimes, the phishing email may seem to come from a high-ranking official within the organization, like a CEO or CFO, requesting urgent action, like transferring funds or providing confidential information. This is known as spear phishing and targets specific individuals with tailored messages.
In organizations, phishing emails might bypass basic email filters, but more advanced email security solutions can flag them based on sender reputation, link analysis, and other heuristic checks.
Hovering over links without clicking can reveal the true destination URL, which is often a quick way to spot a phishing attempt.
A general rule of thumb is if an email seems suspicious or too good to be true, it likely is a phishing attempt. It’s always safer to verify the authenticity of the message through other channels before taking any action.
Phishing attempts have seen a steady increase, with over 3.4 billion phishing emails sent daily.
Types of Phishing Attacks
There are several types of phishing attacks, including:
- Email phishing: An attacker sends an email that appears to be from a legitimate organization, such as a bank or online retailer, and asks the recipient to click on a link or provide personal information.
- Spear phishing: A targeted form of phishing that is directed at a specific individual or organization. The attacker may use personal information or specific details about the target to make the email or message seem more legitimate.
- Whaling: A type of spear-phishing attack that targets high-profile individuals within a company or organization, such as a CEO or CFO.
- Vishing: An attack in which the attacker uses a phone call to try to gather personal information.
- Smishing: Similar to phishing, but the attacker uses text messages to try to trick the victim into providing personal information.
- Clone phishing: An attack in which the attacker creates a copy of a legitimate email or message and changes the link or attachment to direct the victim to a fake website or download malware.
- Website forgery: An attacker creates a fake website that appears to be a legitimate website and uses it to collect personal information from unsuspecting visitors.
- Search engine phishing: An attacker creates a fake website and uses SEO techniques to make it appear on the top of the search engine result page.
These are some examples of phishing attacks, but new types of phishing may emerge with the advance of technology.
Phishing Survey
Email Phishing
Email phishing is a form of cyber attack where attackers masquerade as trustworthy entities in digital communications, primarily through emails. The primary aim is to trick individuals into divulging sensitive information like login credentials, credit card numbers, or to install malware on the victim’s system.
In a typical phishing attempt, an attacker crafts an email that appears to be from a legitimate source, such as a bank, a well-known company, or even a colleague or friend. This email usually contains urgent language, prompting the recipient to take immediate action, such as clicking on a link or opening an attachment. These links often lead to fake websites, meticulously designed to mimic legitimate ones, where any information entered by the victim is captured by the attackers.
Attachments in phishing emails can be equally dangerous. They might contain malware, such as Trojans, ransomware, or spyware, which gets installed on the user’s device upon opening the file. This malware can then perform a range of malicious activities, from encrypting the user’s data for ransom to silently harvesting sensitive information over time.
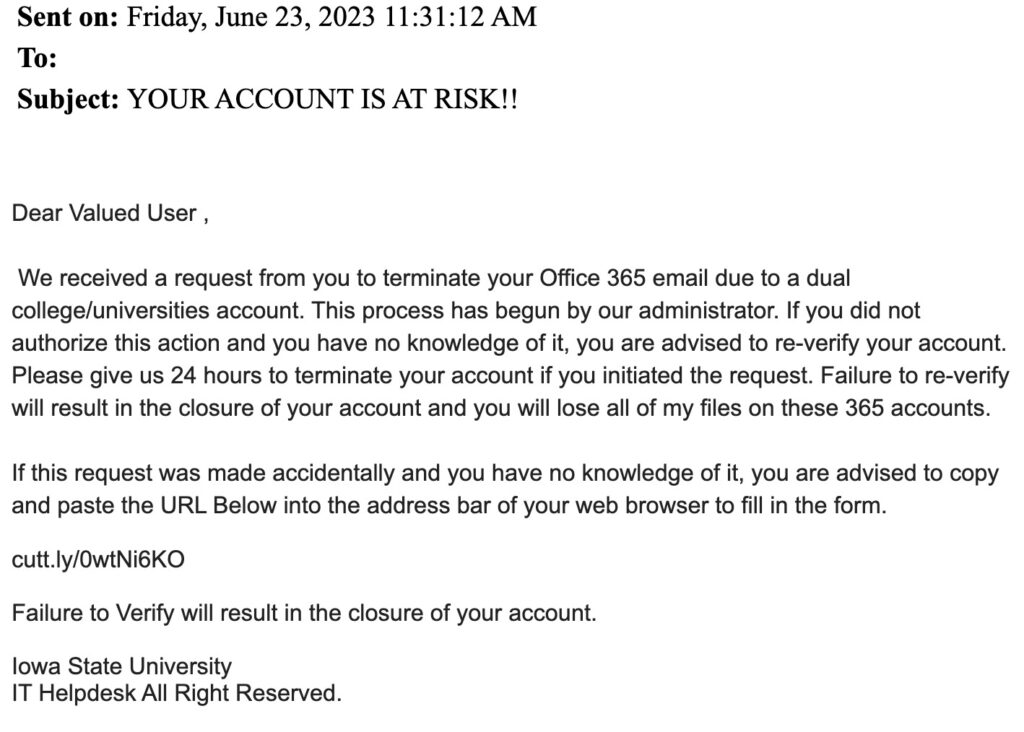
Spear Phishing
Spear phishing represents a more targeted form of phishing, where attackers specifically tailor their deception to a particular individual, organization, or business. Unlike traditional phishing, which is more of a broad and scattergun approach, spear phishing involves in-depth research and personalization to increase the likelihood of a successful attack.
In spear phishing, attackers often gather information about their target before launching the attack. This information can include names, job titles, email addresses, information about their colleagues, and specific details about their work or personal life. Sources for this information can range from social media profiles and corporate websites to leaked or stolen data from previous breaches.
The emails used in spear phishing campaigns are highly personalized and can be extremely convincing. They might mimic the tone, language, and email format of communications familiar to the target, making them appear legitimate. The email might appear to come from a trusted sender – a colleague, a superior, or a well-known business contact – which adds to the deception.
These emails usually create a sense of urgency or a compelling reason for the target to take immediate action. This action could be clicking on a link, which leads to a fake website designed to steal login credentials or other personal information, or opening an attachment that installs malware on the victim’s device.
The malware used in spear phishing can be varied, including ransomware, spyware, or software that allows the attacker to gain control of the victim’s computer. This can lead to a variety of outcomes, such as data theft, financial loss, or further attacks within an organization.
One of the most insidious aspects of spear phishing is its ability to bypass traditional security measures. Since the emails are highly personalized and do not exhibit typical phishing characteristics, they can often evade email filters and anti-phishing software. This makes user education and awareness an essential component of defense against spear phishing.
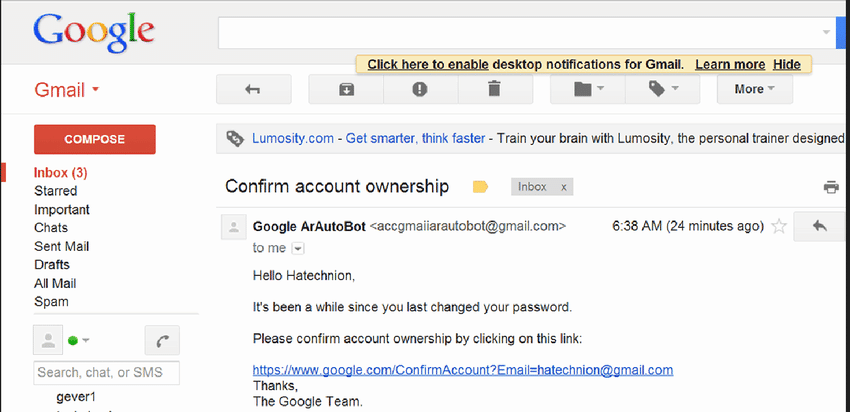
Whaling
Whaling is a specific form of phishing that targets high-profile individuals within an organization, such as C-level executives, managers, or other key decision-makers. This technique is named ‘whaling’ due to the high value of the targeted individuals, analogous to the size and value of whales compared to smaller fish.
The primary objective in whaling is to deceive these high-ranking officials into disclosing sensitive company information, transferring funds, or providing access to restricted systems or data. Due to the high stakes involved, whaling attacks are typically well-researched and crafted with a greater degree of sophistication compared to standard phishing attacks.
In a whaling attack, the content of the email or communication is tailored to the specific role, interests, and responsibilities of the targeted individual. The attackers often gather detailed information about the target, such as their work habits, communication style, and professional contacts. This information can be sourced from corporate websites, social media profiles, and other publicly available data.
The attack might involve emails that mimic internal correspondence, appearing to come from other executives or important external partners. These emails often address company-specific issues, financial matters, or legal concerns, lending an air of legitimacy and urgency. They may include requests for wire transfers, confidential financial reports, or sensitive personnel information.
Whaling emails often bypass conventional email filters due to their personalized and seemingly legitimate nature. They do not typically contain suspicious links or attachments, which are common indicators of phishing. Instead, they rely on social engineering and manipulation of trust to achieve their goals.
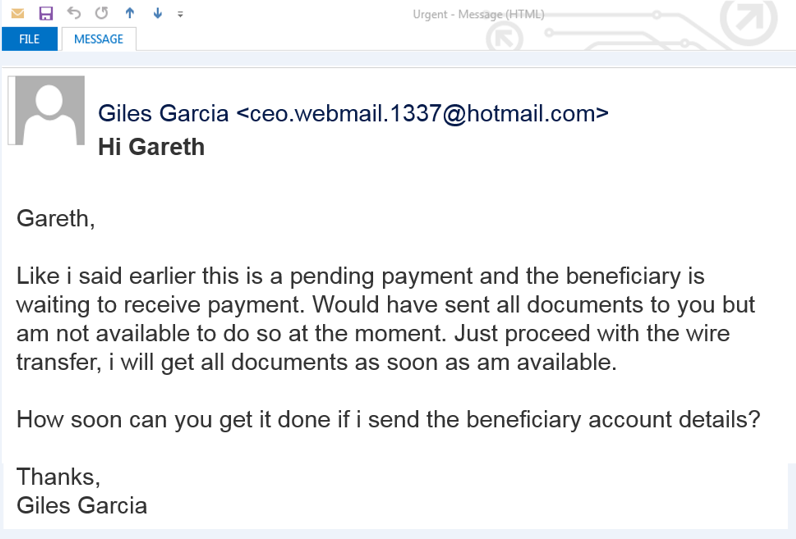
Vishing
Vishing, short for “voice phishing,” is a fraudulent practice where attackers use phone calls to trick individuals into divulging sensitive information or performing actions that compromise their security. This technique exploits the trust people typically place in voice communications compared to other forms, like email.
Attackers use various tactics in vishing calls. They might impersonate representatives from legitimate organizations, such as banks, government agencies, or tech companies. By creating a sense of urgency or authority, they manipulate victims into sharing personal details, financial information, or access credentials. Common scenarios include false claims about unauthorized bank transactions, tax issues, or computer security threats.
Technology plays a significant role in vishing. Attackers often use caller ID spoofing to make it appear as if the call is coming from a legitimate source, enhancing the illusion of authenticity. Voice over IP (VoIP) technology enables them to make these calls cheaply and anonymously, often from different countries, making it harder to trace and prosecute the perpetrators.
Social engineering is a key component of vishing. Attackers do their homework, sometimes gathering personal information about their targets beforehand to make their claims more convincing. This pre-attack research can involve mining social media profiles, public records, or data obtained from previous breaches.
Unlike phishing emails, vishing does not leave a digital trail like a suspicious link or attachment, making it more challenging to identify and report. The real-time interaction in a phone call also pressures the victim to react immediately, which can lead to hasty decisions without proper verification.
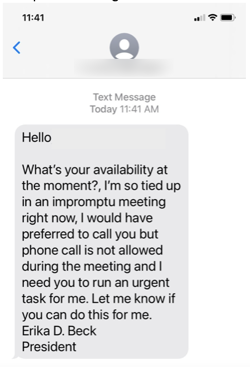
Smishing
Smishing, derived from “SMS phishing,” is a type of phishing attack where fraudsters use text messages (SMS) as the medium to trick recipients into revealing personal information, downloading malware, or participating in fraudulent activities. Unlike email phishing, smishing exploits the SMS platform, which can lend an air of immediacy and legitimacy to the messages.
In a typical smishing attack, the perpetrator sends a text message that appears to be from a legitimate source, such as a bank, government agency, or a familiar service provider. These messages often create a sense of urgency, prompting the recipient to act quickly. Common tactics include alarming the recipient about a security breach, promising rewards, or notifying them of a supposed package delivery.
The malicious content in smishing messages can take various forms. Some messages may contain links to fraudulent websites designed to capture personal information like login credentials or financial details. Others might encourage the recipient to download an application, which is actually malware. This malware can then perform a range of actions, from stealing sensitive information to enlisting the device in a botnet.
Smishing attacks exploit the widespread use of smartphones and the tendency of users to trust text messages over emails. The personal nature of text messaging can make recipients less vigilant about verifying the source and content of messages they receive.
One of the technical challenges in combating smishing is the limited ability of SMS to carry sophisticated security features. Unlike emails, text messages cannot display detailed sender information or support advanced security protocols, making it more difficult for users to discern legitimate messages from fraudulent ones.
Phishing Attack Prevention and Protection
There are several steps you can take to protect yourself from phishing attacks:
- Be suspicious of unsolicited emails or messages, especially if they ask for personal information. Legitimate organizations will not typically ask for sensitive information through email or instant messaging.
- Be wary of clicking on links or downloading attachments from unknown sources. These can be used to install malware or direct you to a fake website.
- Use antivirus software and a firewall to protect your computer from malware.
- Use multi-factor authentication when possible, as this adds an extra layer of security to your accounts.
- Keep your software and operating system up-to-date with the latest security patches.
- Educate yourself about the different types of phishing attacks and how to recognize them.
- Be vigilant and do not respond to suspicious messages.
- Use a password manager to generate and store unique, strong passwords for each of your online accounts.
- Be cautious when providing personal information online, and always check the URL of a website to make sure it is legitimate.
- Keep an eye on your bank account and credit report for any suspicious activity.
2024 Data Sources
- https://consumer.ftc.gov/articles/how-recognize-and-avoid-phishing-scams
- https://www.irs.gov/privacy-disclosure/report-phishing
- https://www.cisa.gov/secure-our-world/recognize-and-report-phishing
- https://www.secretservice.gov/
investigation/Preparing-for-a-Cyber-Incident/phishing - https://csrc.nist.gov/glossary/term/phishing
- https://www.cms.gov/files/document/best-practices-cybersecurity-phishing.pdf